Traversable Edges
Most edges in BloodHound are traversable, representing a relationship between two nodes where the starting node can take control of the ending node to a degree that allows an attacker to abuse outgoing edges. For example, consider the ForceChangePassword edge: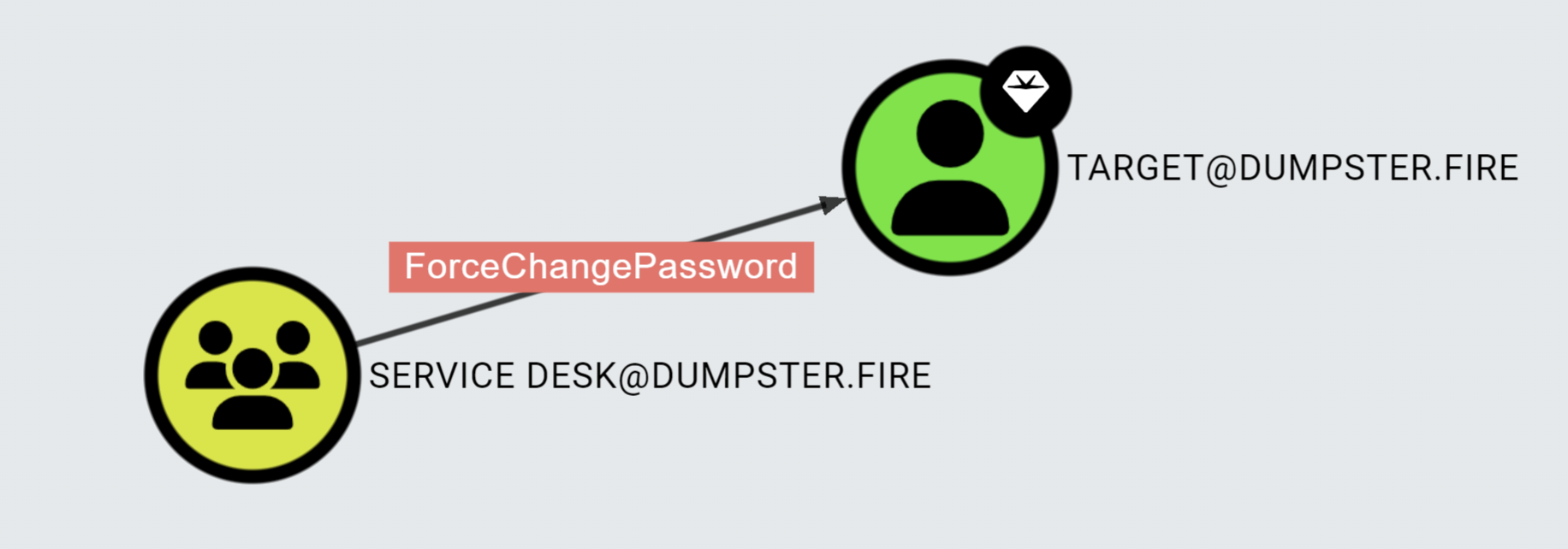
Non-Traversable Edges
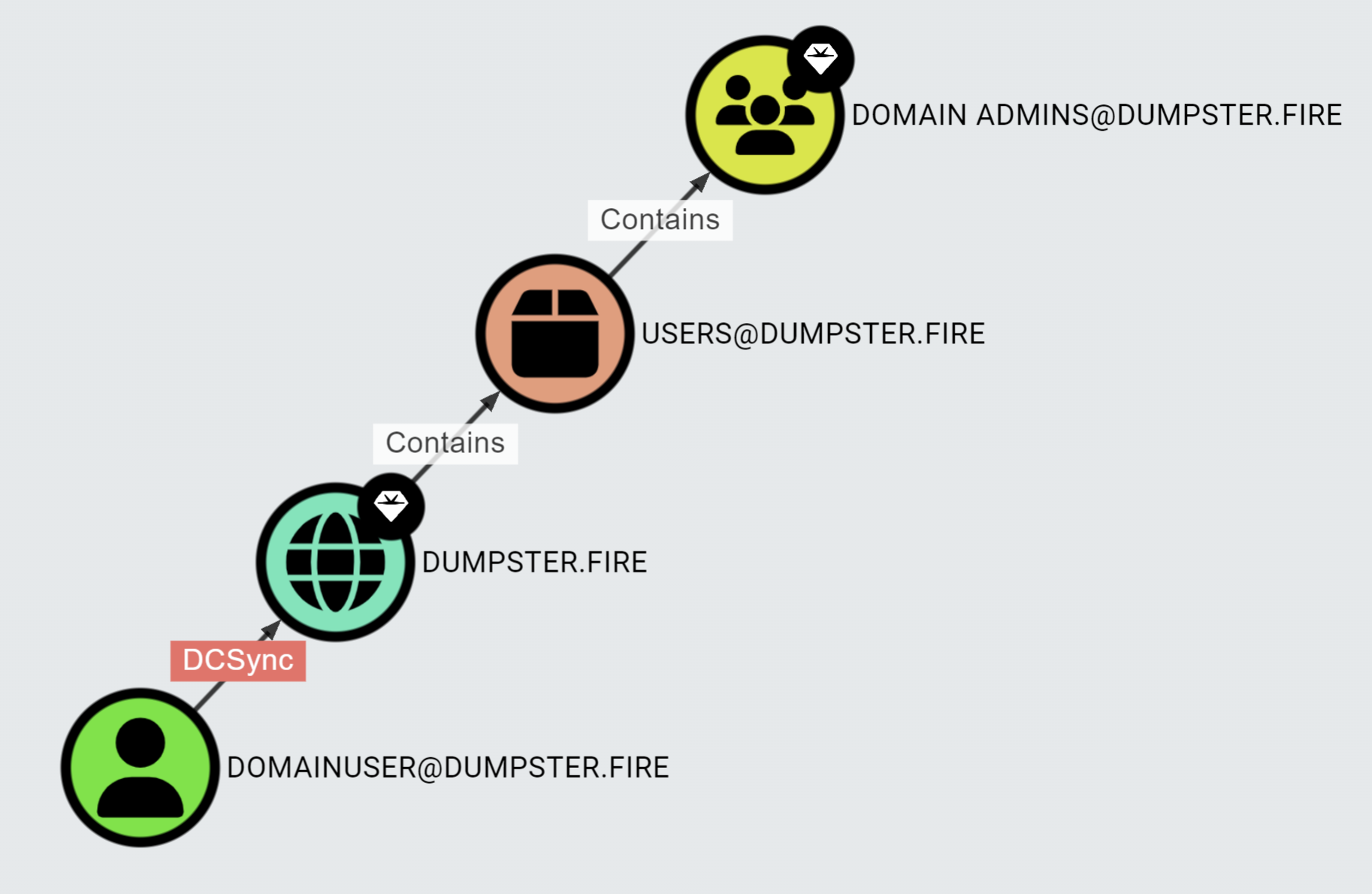
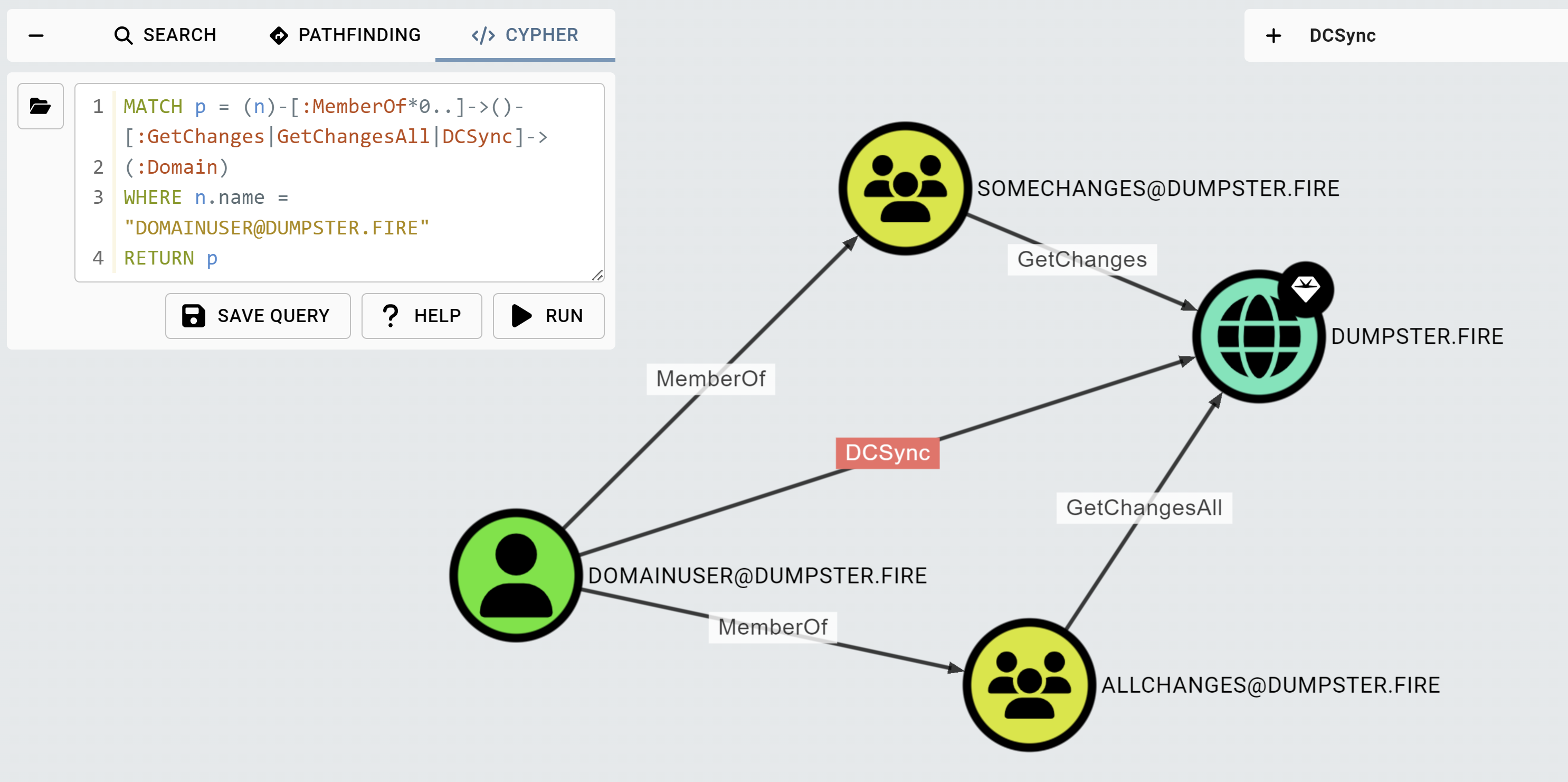
If you cannot abuse a given relationship between two nodes to take control of the end node, then the relationship is non-traversable. However, some non-traversable relationships can form a traversable relationship when combined. An example is the DCSync attack narrative. GetChanges and GetChangesAll permissions on the domain object combined enable you to perform the DCSync attack. GetChanges and GetChangesAll are non-traversable edges, and BloodHound uses them to produce the traversable DCSync edge in what we call the post-processing logic. Pathfinding includes only traversable edges. As a result, you might get a DCSync edge in a path like this: