Configure SharpHound Enterprise Client for Cross-Trust Collection
When configuring a SharpHound Enterprise client, it is possible to specify additional domains to be collected by entering domain names in “Scope Collection to Multiple Domains”. Alternatively, the SharpHound Enterprise client can collect from all domains trusting the service account domain by checking the option “Collect from all domains trusting the SharpHound service account, including transitively”. This option will also collect from trusting domains in other forests.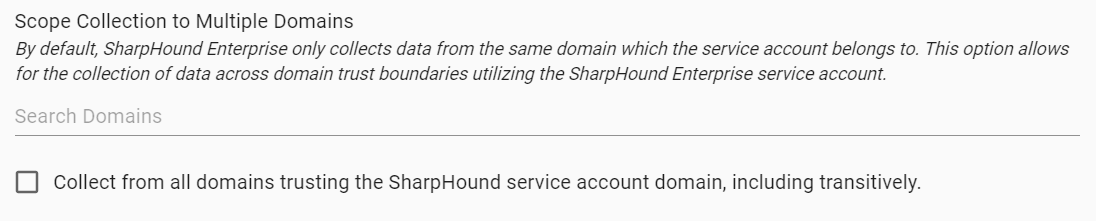
Collection Across External Trust
Kerberos authentication works by default for all Active Directory trust types except external trusts. SharpHound Enterprise supports collection across external trusts via two mechanisms.Forest Search Order (preferred)
Administrators can enable Kerberos authentication across external trusts by adding the name of the other domain to the Use forest search order policy setting on Domain Controllers.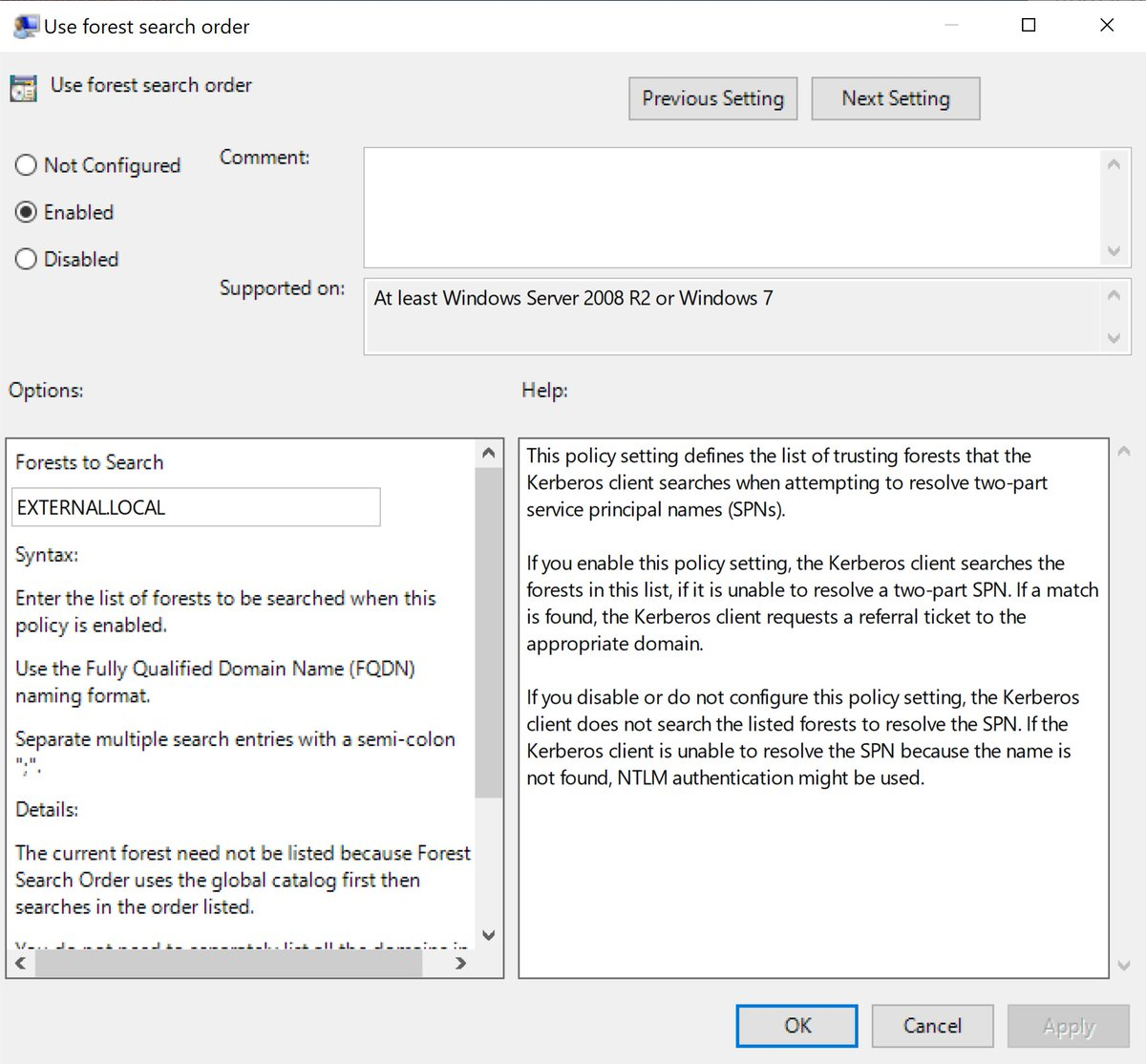
LDAP Authentication Auto-Negotiation
SharpHound Enterprise will, by default, only support Kerberos authentication for the LDAP connections to Domain Controllers for Active Directory Structure Data collection. This will cause the collection across the external trust to fail without modifying SharpHound’s default behavior in the configuration file “settings.json”. The configuration file default path is described in SharpHound Enterprise Local Configuration. To enable support for auto-negotiation in LDAP connections:- Stop the SharpHound Delegator service.
- Open settings.json as an Administrator (right click -> Run as Administrator on notepad.exe)
- Change the ForceLDAPKerberosAuth setting to False (no quotes)
- Save settings.json
- Start the SharpHound Delegator service.
Troubleshoot Cross-Trust Collection
The collection across a trust will fail if:- The Kerberos-supported encryption types between domains/forests do not match.
- Authentication has been restricted, e.g., using authentication policy silos or IPSec.
- There is no network access from the SharpHound server to the trusting domain’s DCs and domain-joined Windows systems in scope for privileged collection.