Recommended hardening
gMSA
We recommend using a Group Managed Service Account (gMSA) for the SharpHound service account rather than a regular AD user. Follow the article: Create a gMSA for SharpHound. A gMSA is a type of service account where the password is managed by Active Directory, eliminating the need for manual password management. This will ensure the service account password is:- A 240-byte randomly generated complex password
- Not known to any individuals nor stored in any notes, password vault, etc.
- Rotated regularly
Protected User group
We recommend adding the SharpHound service account as a member of the Protected Users group. Protected Users is an AD security group designed to reduce credential exposure. Members of this group automatically have non-configurable protections applied to their accounts. Protected Users members cannot be delegated with Kerberos and cannot authenticate using NTLM, effectively remediating Kerberos delegation attacks, NTLM relay attacks, and NTLM cracking. However, Microsoft advises against adding service accounts to the group as authentication for the service account may fail. Our testing has shown that adding the SharpHound service account to Protected Users works if the SharpHound service account is a gMSA, but the SharpHound service crashes after four hours if it is a regular AD user.Tiering SharpHound
We recommend tiering the SharpHound service account to follow the principle of “elevated user accounts should not be used to log on to lower Tier assets”. Follow the article: Tiered SharpHound Strategy. This recommendation is especially for organizations seeking to implement the Active Directory Tier Model or Enterprise Access ModelAttacks and remediations
This section explores the types of attacks that SharpHound Enterprise may be at risk of, all of which are mitigated with the recommended hardening.Attack 1: Finding/guessing service account password
When a service account is created as a regular AD user, the person creating the account must set a password for the service account and must store this password somewhere. Attackers will attempt to obtain the password by guessing/spraying with common passwords and passwords of other accounts in the environment. They will also look for service account passwords in file shares, key vaults, etc.Preferred remediation: gMSA
When the service account is created as a gMSA, the password will be managed completely by AD. That means the password of the account cannot be a weak/guessable password, and it will not be stored anywhere the attacker can gain read access.Alternative remediation: Strong password stored securely
When the password is strong, it decreases the risk of an attacker guessing the password. The SharpHound service account password can be copy-pasted when installing SharpHound Enterprise. Setting the password to a random string of 100 characters will therefore not cause inconvenience. The password should be stored securely in a password vault where only the right personnel have access.Attack 2: Kerberos delegation attacks
When collecting data, the SharpHound service account will only perform a network logon (type 3) on remote computers. This logon type will not save the service account credentials in the remote computer’s memory. However, Kerberos delegation breaks this rule if the remote computer is configured with Kerberos unconstrained delegation. In that case, the remote computer will receive a copy of the service account’s Kerberos session ticket (TGT), which an attacker can extract from memory and utilize to authenticate as the service account. If the computer is configured with unconstrained delegation, the service account does not need to log on to the computer – the attacker can obtain service tickets as any user for services it is allowed to delegate to.Preferred remediation: Protected Users group (gMSA only)
Members of the Protected Users group cannot be delegated, as described by Microsoft here. This means the SharpHound service account will not be vulnerable to the Kerberos delegation attacks. This remediation will break the SharpHound service if a regular AD user is used instead of a gMSA.Alternative remediation: Mark the account as sensitive
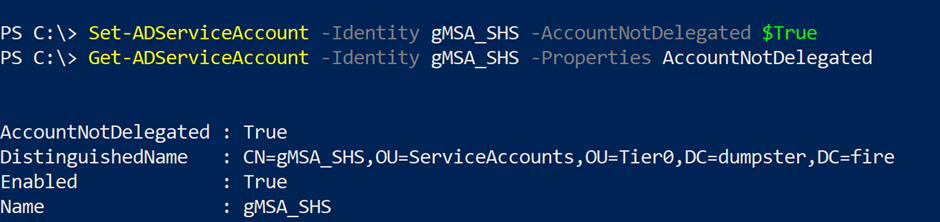
It is possible to prevent an AD principal from using Kerberos delegation services by enabling the account option “Account is sensitive and cannot be delegated”: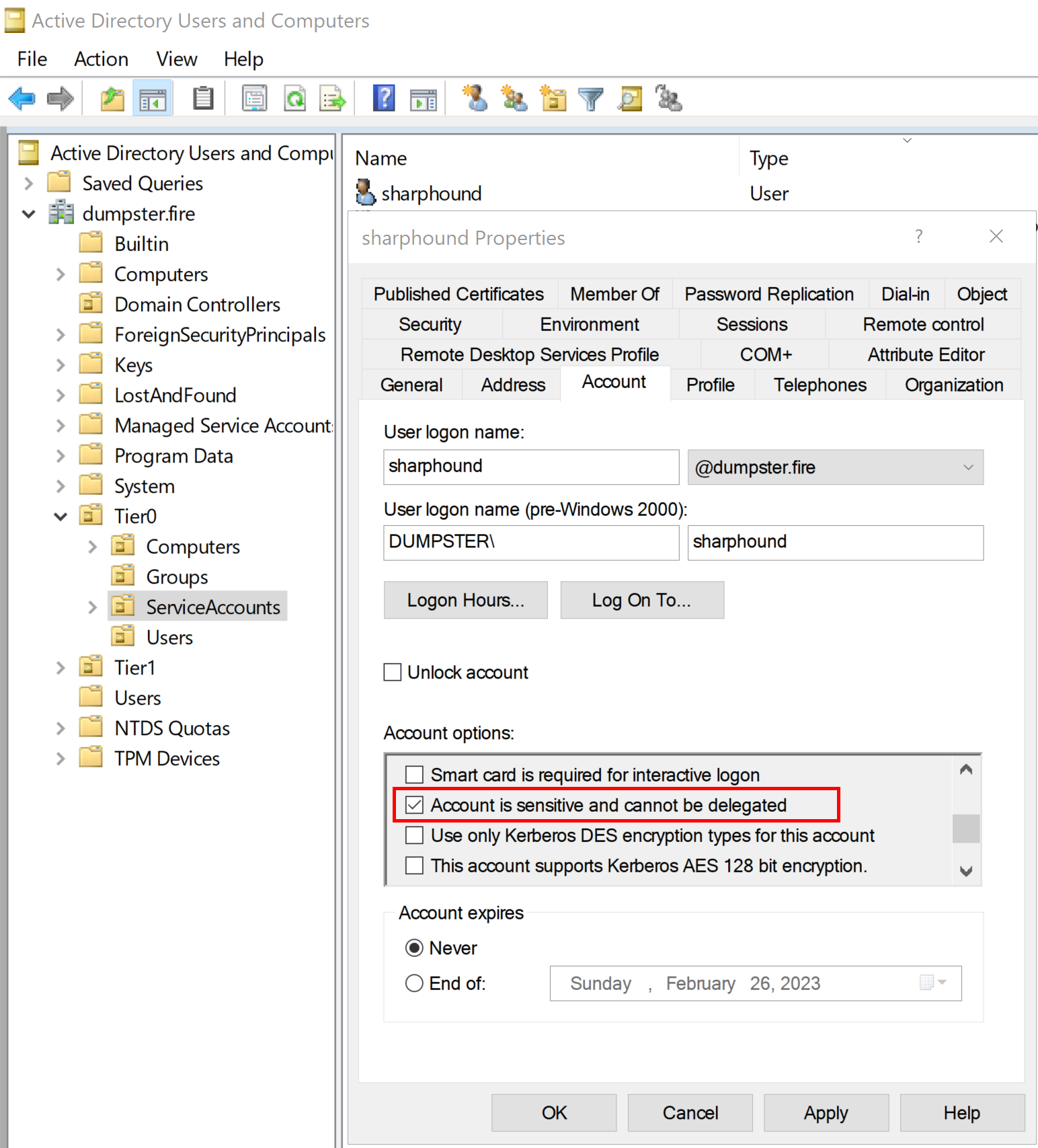
Attack 3: Authentication relaying
The data collection performed by the SharpHound service account happens over the SMB protocol and is authenticated on the remote computer using Kerberos by default. However, an attacker with administrative rights on the remote computer can downgrade the authentication to NTLM. This allows the attacker to perform an NTLM relay attack, where the ongoing NTLM authentication is relayed to a target computer, giving the attacker a session on the target as the SharpHound service account. It is possible to relay Kerberos authentication under specific circumstances, but we have not found it to be possible with the SharpHound service account.Preferred remediation: Protected Users group (gMSA only)
Members of the Protected Users group cannot authenticate with NTLM, as described by Microsoft here. This means the SharpHound service account will not be vulnerable to NTLM attacks. This remediation will break the SharpHound service if a regular AD is used instead of a gMSA.Alternative remediation: Block outgoing NTLM
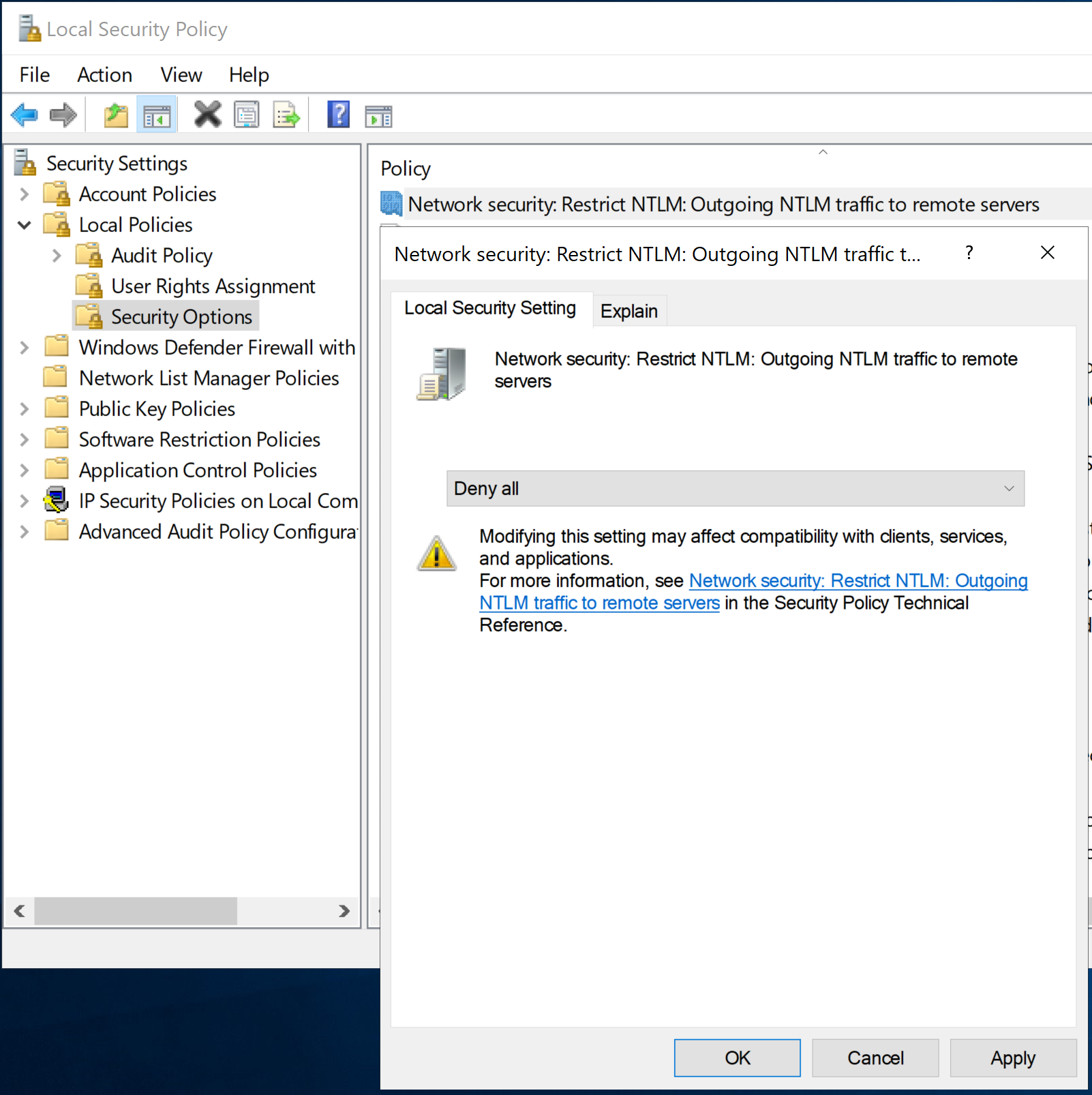
Outgoing NTLM can be denied entirely from the SharpHound server by configuring the security option Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers to Deny All: