Overview of gMSAs
Group Managed Service Accounts (gMSA) are managed domain accounts that provide automatic password management, simplified service principal name (SPN) management, and the ability to delegate the management to other objects. Detailed software requirements from Microsoft are available here. Microsoft gMSA documentation is available here.Create a gMSA account
To create a gMSA account, start by preparing the domain.- Log into a domain controller within the domain you want to create a gMSA.
-
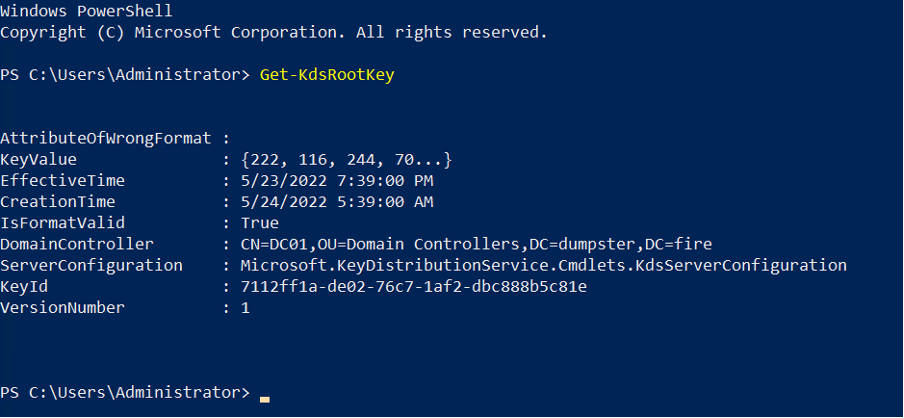
To validate whether the domain has a KDS Root Key configured, run:
If there’s no result returned, the KDS Root Key has not been configured in the domain. Continue on to step 3. If there is a result returned, the KDS Root Key has already been configured in the domain. Skip step 3 and move on to Create the gMSA and password read group.
-
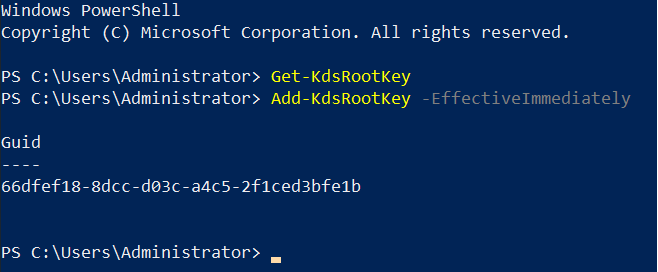
Create the KDS Root Key.
For a production environment, run:
For a test environment, make the key available for immediate use by running:
Create the gMSA and password read group
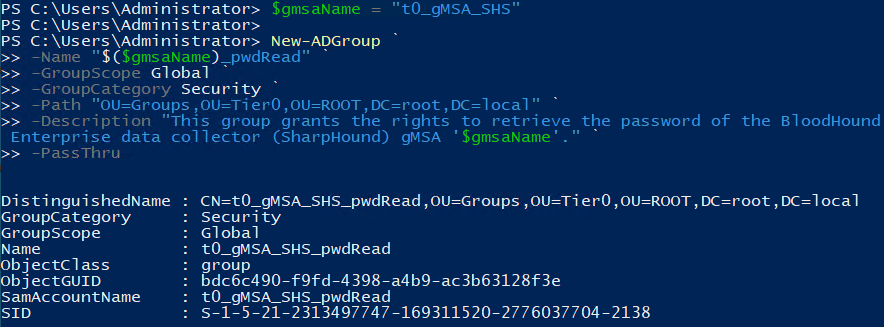
Perform these steps from/against a writeable Domain Controller.- Create a gMSA password read group for computers that should have access to the gMSA password. Browse to the desired location in Users and Computers and create the group. Alternatively, use this template to create the group using PowerShell:
-
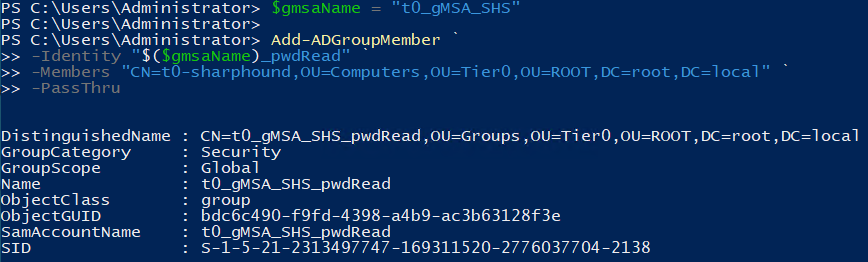
Add the SharpHound server that performs the Sharphound collections as a member of the gMSA password read group. This allows it to access the password of the gMSA and run the service.
Add the computer to the group in Users and Computers.
Alternatively, use this template to add group membership using PowerShell:
When viewing the changes on a Windows server with the GUI enabled, you can see the OUs and the t0_gMSA_SHS_pwdRead group you created.
-
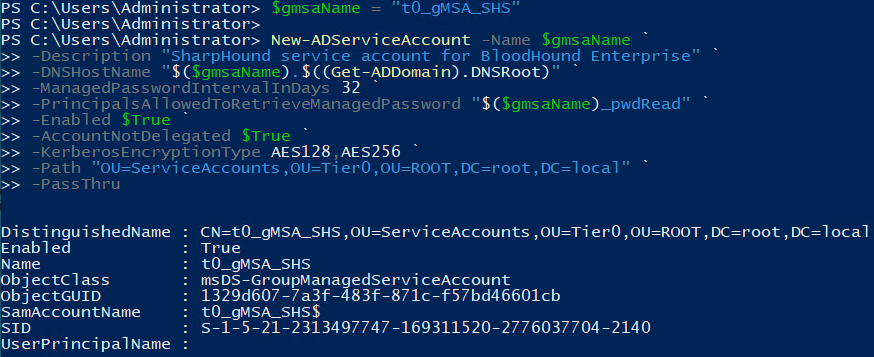
Create the gMSA and allow the password read group to retrieve its password.
On a Domain Controller, use this template to create the gMSA and set the retrieve right using PowerShell:
Prepare the SharpHound server
- Restart the SharpHound Enterprise server so that the server’s membership of the `pwdRead` group takes effect.
- Grant the gMSA the “Log on as a service” User Rights Assignment on the SharpHound server. This can be done through `secpol.msc` or policy deployment methods like a GPO.
- (Optional) Test that the SharpHound server can retrieve the gMSA password. See Test the gMSA.
Test the gMSA
Optionally test the gMSA server to make sure that the gMSA is working.-
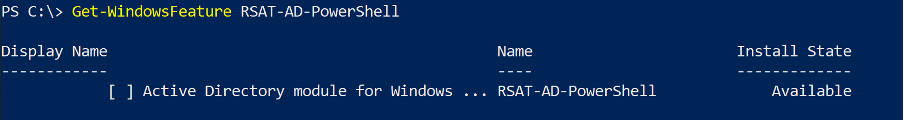
Check the status of the RSAT PowerShell module. On the SharpHound Enterprise server, open a PowerShell as an Administrator and run:
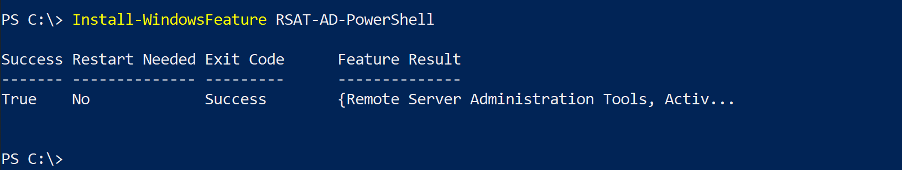
If the Install State shows “Installed”, skip to step 2, otherwise run:
-
In the elevated PowerShell, test that the SharpHound server can retrieve the gMSA password by running:
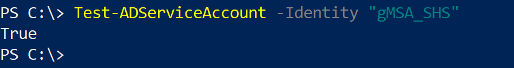
True.
Configure User Rights
As Sharphound is launched with a PowerShell script instead of running as a service, you need to grant the gMSA account the Log on as a batch job User Right instead of the Log on as Service User Right. Do this with the Local Security Policy or Group Policy.Configure user permissions
The Active Directory details collected by SharpHound depend on the permissions that the user running SharpHound has within the Domain. A regular, non-privileged user can run Shaprhound and collect a significant amount of information, but some of the Edges can only be collected by users with elevated permissions within the Domain. At this time there are two main paths that could give the SharpHound gMSA account the permissions needed to collect the required Active Directory information:- Method 1: Make the SharpHound gMSA account a member of the Local Administrators group on all computers in the domain.
- Method 2: Make the SharpHound gMSA account a member of the Domain Admins group.
Implement gMSA account protections
Regardless of whether the permissions that are given to the SharpHound gMSA account are using Method 1 or Method 2, consider additional protections. See SharpHound Enterprise Service Hardening to learn about protections you can implement to prevent the SharpHound gMSA account from being compromised and leveraged by an attacker. The gMSA account should be a member of the Active Directory Protected Users group. Tiering the Sharphound gMSA account access is another methodology you can implement.Configure the gMSA account as a Domain Admin
Add the gMSA account to the Domain Admins group.The account has a
$ at the end of it. Enter the account in this format when adding it to the Domain Admins group.Create a SharpHound PowerShell script to run as a scheduled task
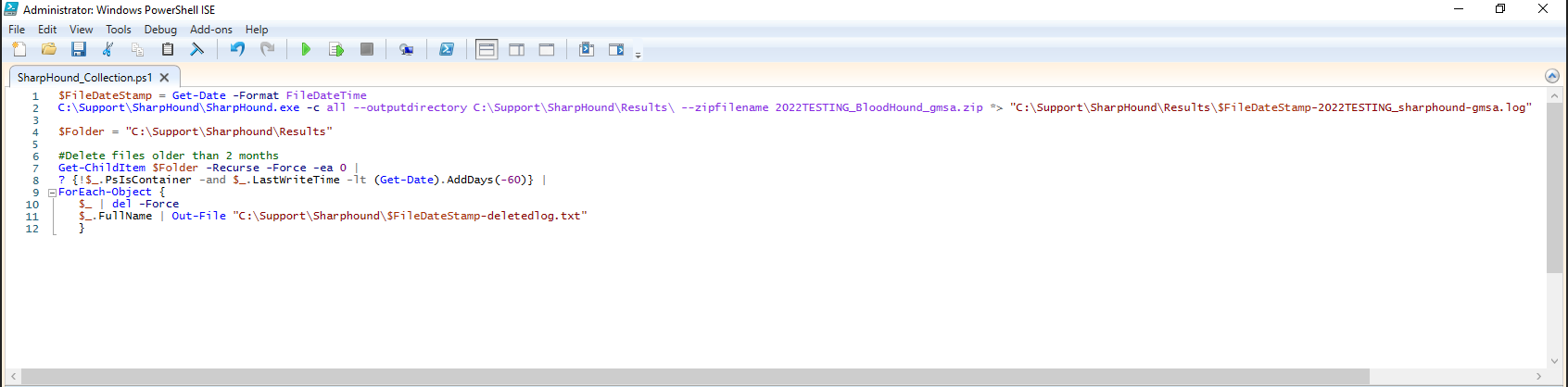
Create a PowerShell script to run SharpHound with a scheduled task.Create a script
To create the script:-
Create a directory named
Sharphoundin theC:\Supportdirectory. -
Create a sub-directory named
Resultsin theC:\Support\Sharphounddirectory. -
Copy the Sharphound executable to the
C:\Support\Sharphounddirectory on the server where the scheduled task runs (the Sharphound executable should be zipped in a password protected zip file so that it doesn’t get prevented by Microsoft Defender during the file transfer). The PowerShell script contains:- The full path to the SharpHound executable
- The command line arguments that you want to pass to SharpHound
- Redirection of the output to a log file
- Deletion of files in the
C:\Support\Sharphound\Resultsdirectory that are older than 2 months
-
Save the PowerShell script named
Sharphound_Collection.ps1to theC:\Support\Sharphounddirectory. - Modify the names of the base —zipfilename and the log file for each specific domain where this is deployed.
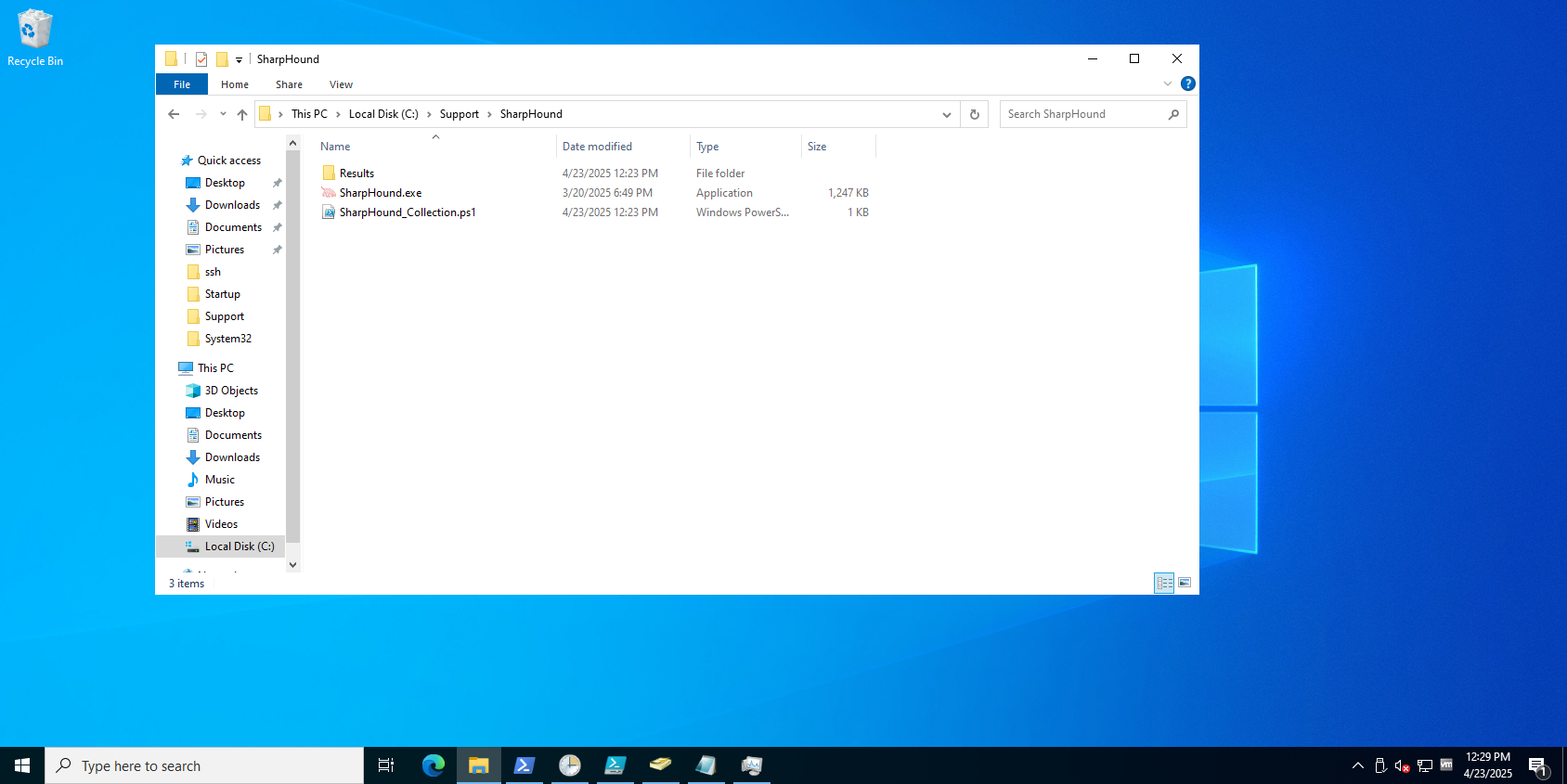
SharpHound_Collection.ps1 PowerShell script should resemble:
Create a scheduled task
To create the scheduled task, choose the PowerShell method or the GUI method. The PowerShell method is the easiest way to create the scheduled task. To create the scheduled task with PowerShell:-
Run these PowerShell commands, modifying files names and domain names as necessary:
-
Construct the PowerShell commands needed for your environment in preparation for executing them in an elevated PowerShell shell.
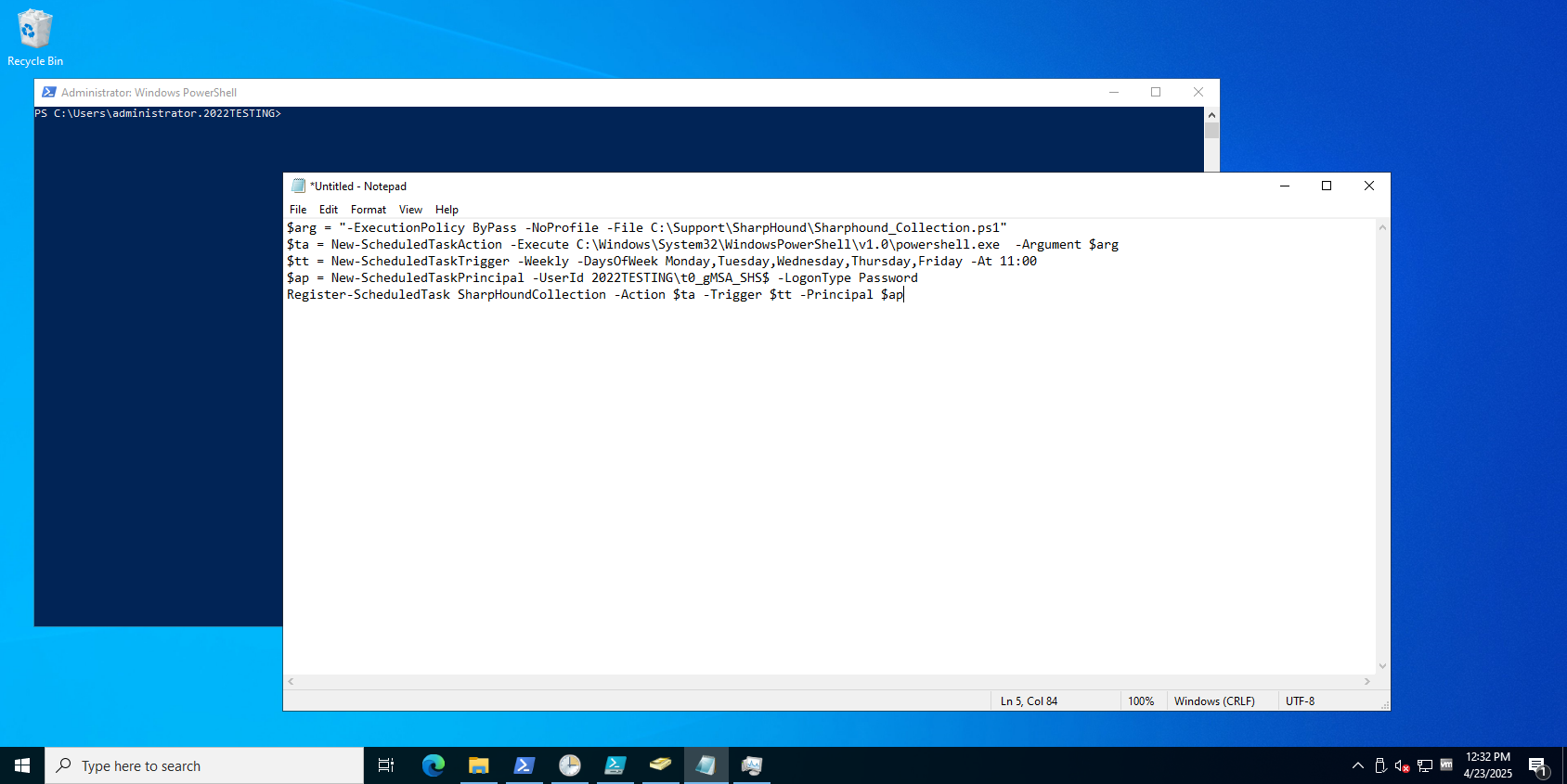
- Copy and paste the PowerShell commands into the elevated PowerShell shell to create the scheduled task.
- After refreshing the Scheduled Tasks MMC, you should see the newly created scheduled task that runs as the gMSA account.
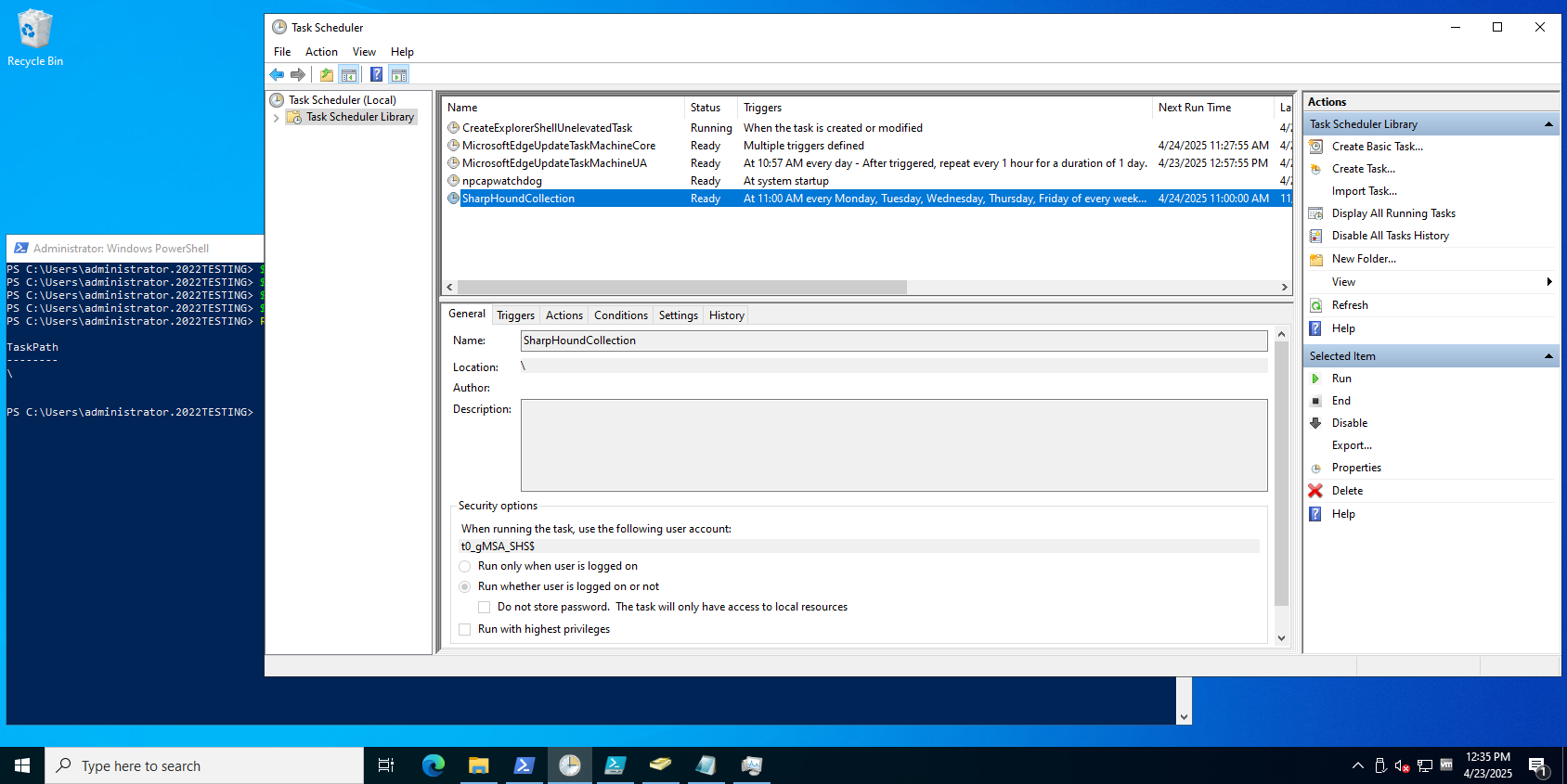
-
Open the Scheduled Tasks MSC on the SharpHound server and create a scheduled task. In the example shown below, the scheduled task name is SharpHound.
- Configure the scheduled task to run on the desired schedule.
-
Configure the scheduled task with this Action:
- Program / script:
powershell.exe - Arguments:
-ExecutionPolicy ByPass -File C:\Support\SharpHound.ps1
- Program / script:
- Click OK on the Edit Action.
- Configure the scheduled task to run as a standard user account at this time.
- Click OK on the scheduled task to complete the creation.
- Provide the password for the standard user account when prompted and click OK.
Modify the scheduled task to run as the gMSA account
At this point you should see the scheduled task setup to run using the user account you previously configured.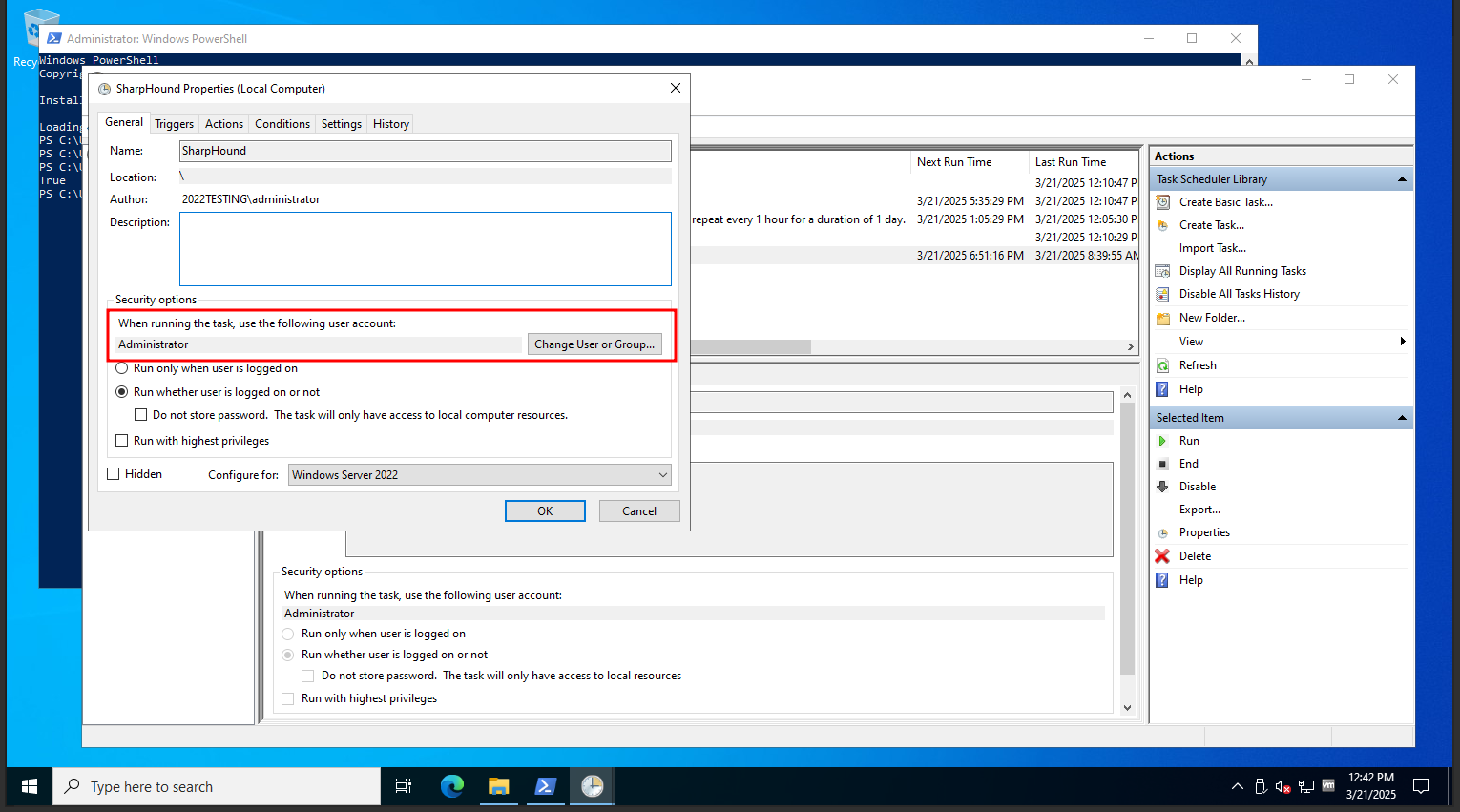
Test the SharpHound scheduled task
To test the scheduled task running as the gMSA account, right click on the scheduled task and click Run. When completed, a zip file should appear with the results. Thank you to @robertstrom for your contribution and permission in modifying your original docs for inclusion in BloodHound’s documentation for other users!