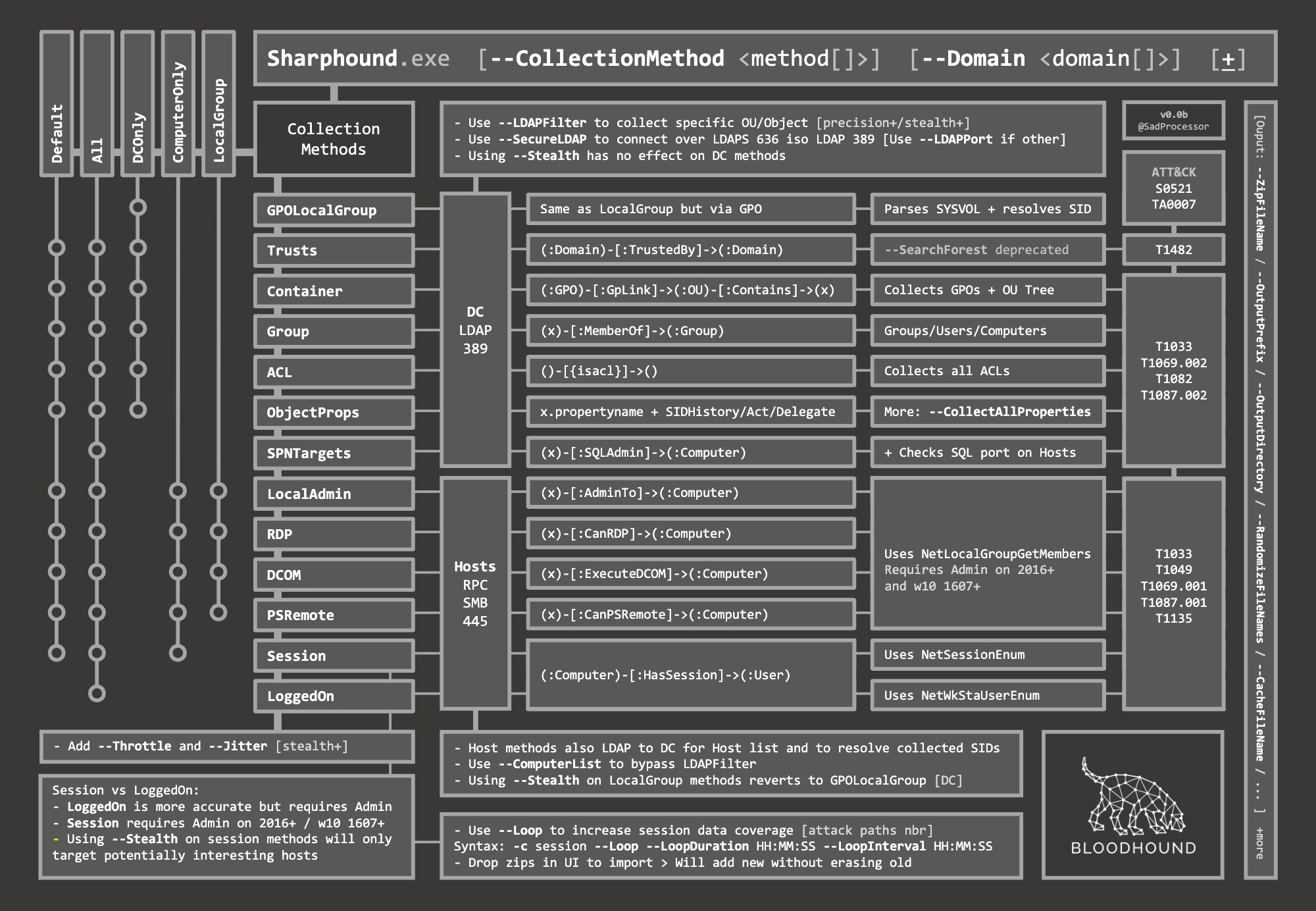
Enumeration Options
CollectionMethods or ‘c’
This tells SharpHound what kind of data you want to collect. These are the most common options you’ll likely use:- Default: You can specify default collection, or don’t use the CollectionMethods option and this is what SharpHound will do. Default collection includes Active Directory security group membership, domain trusts, abusable permissions on AD objects (incl. ADCS objects), OU tree structure, Group Policy links, the most relevant AD object properties, local groups from domain-joined Windows systems, and user sessions.
- All: Performs all collection methods.
- DCOnly: Collects data ONLY from the domain controller, will not touch other domain-joined Windows systems. Collects AD security group memberships, domain trusts, abusable permissions on AD objects (incl. ADCS objects), OU tree structure, Group Policy links, the most relevant AD object properties, and will attempt to correlate Group Policy-enforced local groups to affected computers.
- ComputerOnly: Collects user sessions (Session), local groups (LocalGroup), and User Rights Assignment (UserRights) from domain-joined Windows systems. Additionally, CA registry (CARegistry) data and DC registry (DCRegistry) data is collected. Will NOT collect the data collected with the DCOnly collection method.
- Session: Just does user session collection. You will likely couple this with the
--Loopoption. See SharpHound examples below for more info on that. - LoggedOn: Does session collection using the privileged collection method. Use this if you are running as a user with local admin rights on lots of systems for the best user session data.
- Group: Just collect security group memberships from Active Directory
- ACL: Just collect abusable permissions on objects in Active Directory
- GPOLocalGroup: Just attempt GPO to computer correlation to determine members of the relevant local groups on each computer in the domain. Doesn’t actually touch domain-joined systems, just gets info from domain controllers
- Trusts: Just collect domain trusts
- Container: Just collect the OU tree structure and Group Policy links
- LocalGroup: Just collect the members of all interesting local groups on each domain-joined computer. Equivalent for LocalAdmin + RDP + DCOM + PSRemote
- LocalAdmin: Just collect the members of the local Administrators group on each domain-joined computer
- RDP: Just collect the members of the Remote Desktop Users group on each domain-joined computer
- DCOM: Just collect the members of the Distributed COM Users group on each domain-joined computer
- PSRemote: Just collect the members of the Remote Management group on each domain-joined computer
- ObjectProps - Performs Object Properties collection for properties such as LastLogon or PwdLastSet
- UserRights - Just collect User Rights Assignment from domain computers (needs admin)
- CARegistry - Just collect ADCS properties from registry of Certificate Authority servers
- DCRegistry - Just collect properties from registry of Domain Controller servers
- CertServices - Just collect ADCS objects from Certificate Services
Domain or ‘d’
Tell SharpHound which Active Directory domain you want to gather information from. Importantly, you must be able to resolve DNS in that domain for SharpHound to work correctly. For example, to collect data from the `contoso.local` domain:SearchForest or ‘s’
This flag would instruct SharpHound to automatically collect data from all domains in your current forest.Stealth
Perform “stealth” data collection. This switch modifies your data collection method. For example, if you want to perform user session collection, but only touch systems that are the most likely to have user session data:ComputerFile
Load a list of computer names or IP addresses for SharpHound to collect information from. The file should be line-separated.DistinguishedName
Base DistinguishedName to start search at. Use this to limit your search. Equivalent to the old--OU and ‘—SearchBase’ option.
LDAPFilter or ‘f’
Instruct SharpHound to only collect information from principals that match a given LDAP filter. For example, to only gather abusable ACEs on a user with a certain display name, run this:ExcludeDCs
Instruct SharpHound to not touch domain controllers. By not touching domain controllers, you will not be able to collect anything specified in theDCOnly__ collection method, but you will also likely avoid detection by e.g., Microsoft ATA/ATP.