Entra ID is not currently supported with BloodHound’s OIDC implementation. Use the SAML configuration instead.
Order of Operations
You must configure OIDC in BloodHound in the following order:- Determine the Identity Provider (IDP) name you will use for the OIDC configuration. The same value must be configured in both the IDP and BloodHound. The BloodHound callback URL will include this value.
- Configure the IDP for BloodHound. See the Configure Okta guide for configuring Okta as your OIDC provider.
- Create the OIDC configuration in BloodHound.
- Create new users or modify existing users using the UI or via the newly created OIDC provider.
User Role Mapping
First name, last name, and email are populated when the correct key/value pairs are provided in the assertion payload. A role is applied when the role attribute/claim key is present and its value is a properly formatted BloodHound role. Role values use the prefixbh- and are written in kebab-case. See Administer Users and Roles for capabilities and scopes.
| Role | Key Value |
|---|---|
| Administrator | bh-administrator |
| Power User | bh-power-user |
| Auditor | bh-auditor |
| User | bh-user |
| Read Only | bh-read-only |
| Upload Only | bh-upload-only |
Only one role can be passed per user. If multiple roles are provided, BloodHound ignores them and applies the provider’s default role.
BloodHound Icons
If your IDP supports custom icons for configured applications, please feel free to use the logos below:- Enterprise Dark-colored icon
- Enterprise Light-colored icon
- BHCE Dark-colored icon
- BHCE Light-colored icon
Configure BloodHound
Ensure you have configured an IDP for BloodHound as described in Order of Operations before proceeding.Open the SSO Configuration page
You must be logged in as an Administrator to perform this action.
Enter provider details
Enter the provider details.
| Field | Auth Type | Description |
|---|---|---|
| Provider Name | OIDC and SAML | Name of the SAML or OIDC application in your identity provider; must match exactly |
| Client ID | OIDC only | Client identifier issued by the identity provider |
| Issuer | OIDC only | Issuer URL from the identity provider |
| Metadata File | SAML only | SAML metadata XML from the identity provider |
| Default Role | OIDC and SAML | Role applied when the provider does not supply one |
Create new users on login
Enabling this option will have BloodHound create a new user on the first login with SSO (Just-In-Time). The user will be granted the role passed in the role claim if included, else the default role will be assigned.Allow IDP to modify roles
Enabling this option allows the SSO provider to modify user roles. This is accomplished by updating the role claim associated with the user account. The role will be updated on the next login.Only one role can be passed per user. If multiple roles are provided, BloodHound ignores them and applies the provider’s default role.
Configure Users
By default, all users utilize a username and password via the built-in authentication service. When creating or modifying a user, you can change this setting. When creating a new user, ensure the user does not share an email address with any other users (across all authentication methods).Open the Manage Users page
You must be logged in as an Administrator to perform this action.
Locate a user
Locate the user you want to configure with authentication, click the hamburger menu button on the right side of the row, then Update User.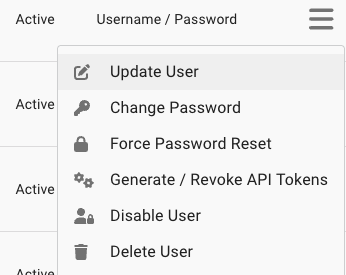

Configure the user for SSO authentication
In the Update User dialog, select the Single Sign-On authentication method, then select the appropriate SSO provider.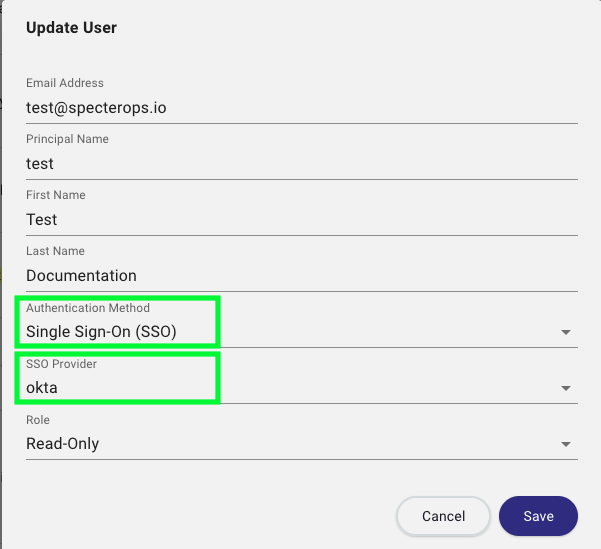

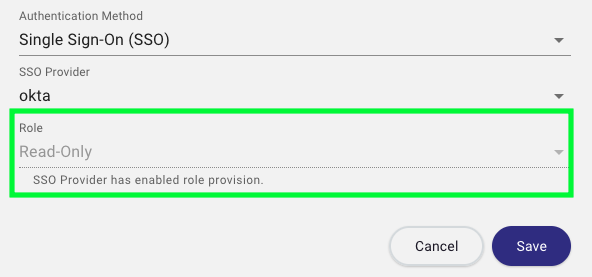
- When Provisioning is enabled without the Modify Role option, a user’s role may be updated manually after creation.
-
If both Provisioning and Modify Role are enabled, role updates must come through the SSO provider (manual updates in BloodHound are disabled).