For platform concepts, terminology, and product capabilities, see the Splunk SOAR documentation.
- Get real-time visibility into attack path findings: View BloodHound Enterprise findings in Splunk SOAR as they are detected.
- Automate response playbooks from BloodHound detections: Trigger investigation and containment workflows automatically when BloodHound Enterprise identifies a risk.
- Reduce manual triage and improve consistency: Standardize repeatable response actions across your existing security tooling.
- Accelerate mitigation of privilege escalation risks: Use automated tasks to respond to high-impact identity threats faster.
Prerequisites
Before you begin the installation and configuration process, ensure the following prerequisites are met:- Admin access to a Splunk SOAR instance
- Access to a BloodHound Enterprise tenant
- BloodHound Enterprise non-personal API key/ID pair with the Auditor role
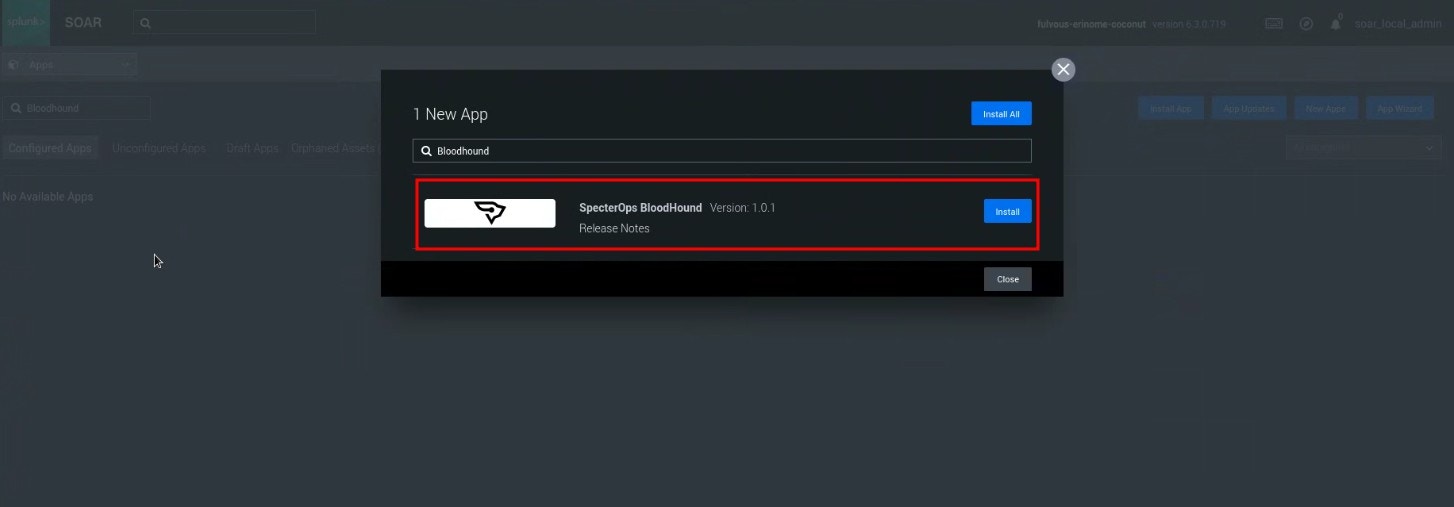
Install the app
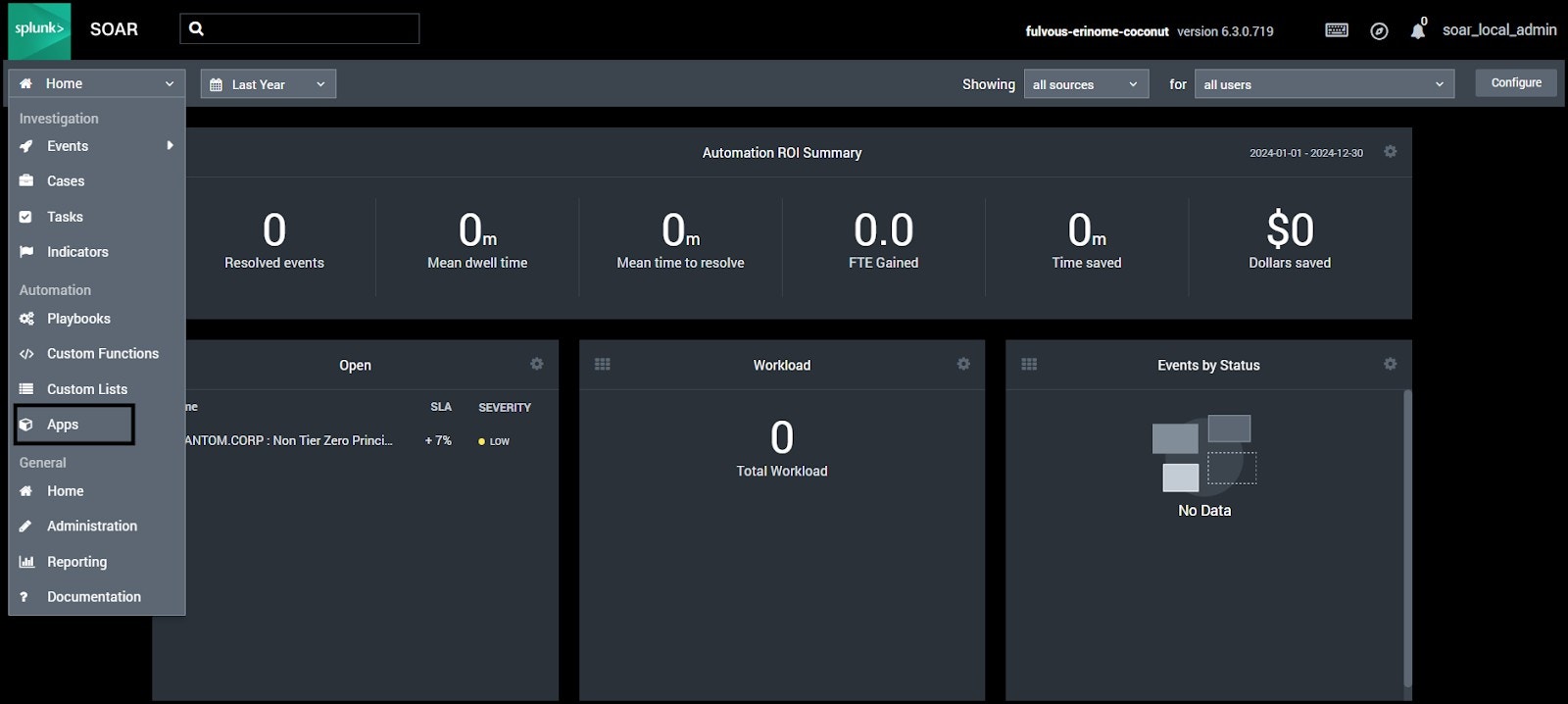
Installing the BloodHound Enterprise for Splunk SOAR app involves the following steps:Navigate to Splunk SOAR
- Log in to your Splunk SOAR instance as an admin.
- Click on the Home dropdown in the top-left corner and select Apps.
Configure the app
After installing the BloodHound Enterprise for Splunk SOAR app, you need to configure it to connect to your BloodHound Enterprise tenant and start ingesting attack path findings. The configuration process involves the following steps:Navigate to app configuration
On the Unconfigured Apps page, click Configure New Asset for the BloodHound Enterprise app.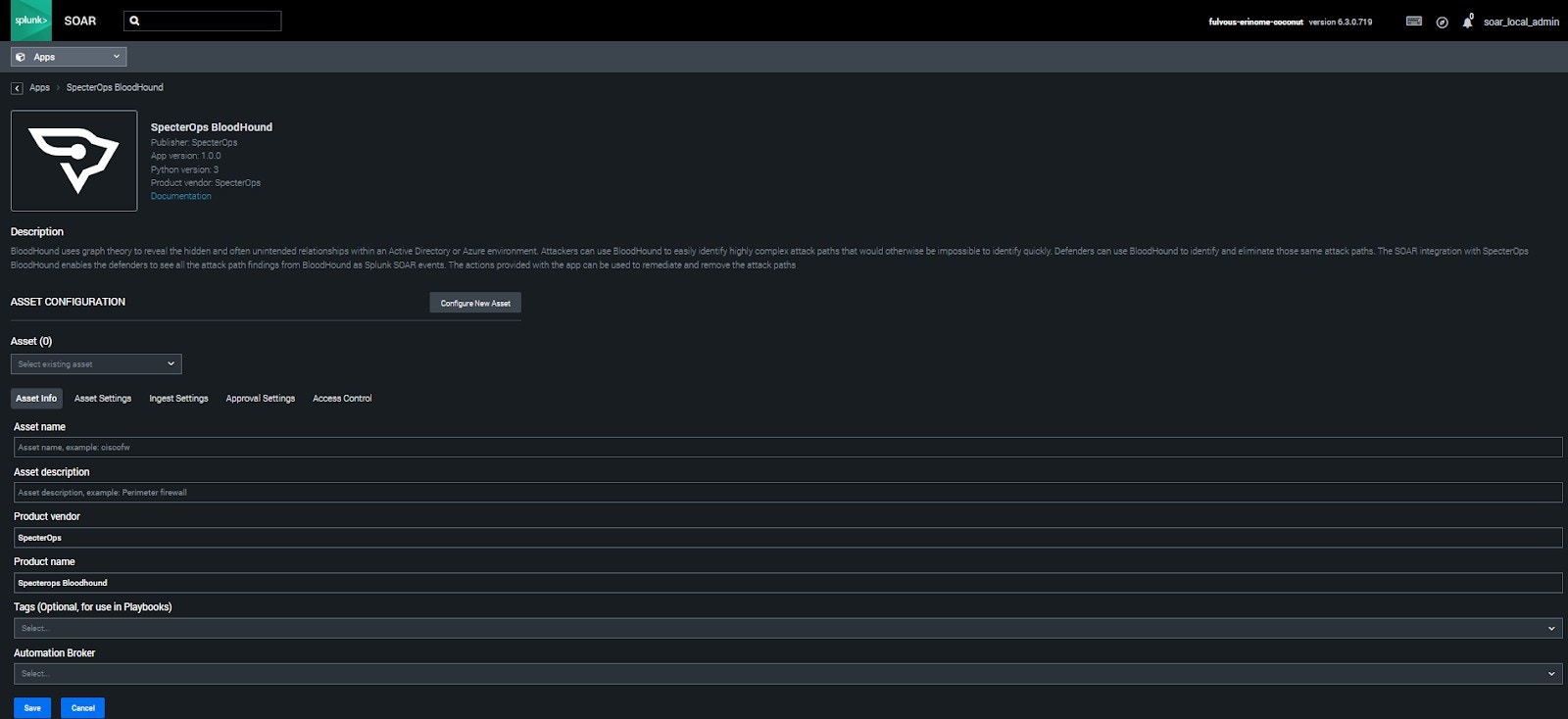

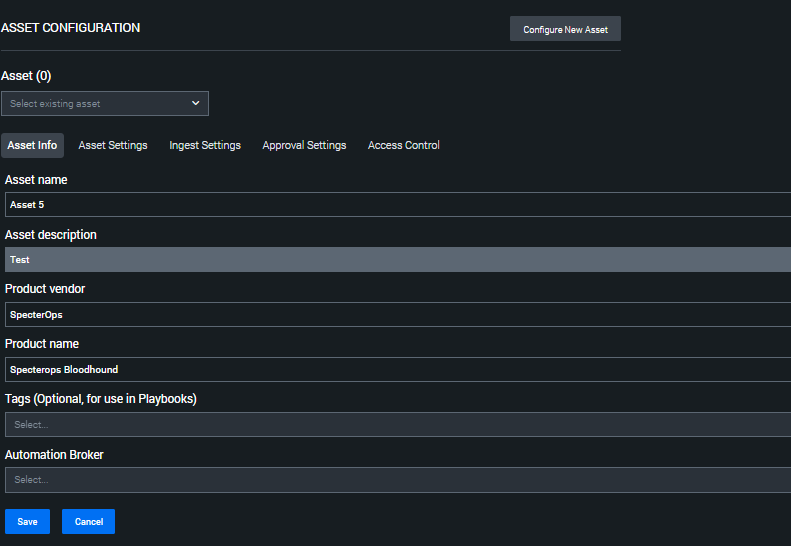
Configure API credentials
- Click Asset Settings to set up the connection to BloodHound Enterprise.
-
Enter the following details:
Field Description BloodHound Enterprise Domain The URL you use to access your BloodHound Enterprise tenant Token Key The token key from your BloodHound Enterprise non-personal API key/ID pair Token ID The token ID from your BloodHound Enterprise non-personal API key/ID pair 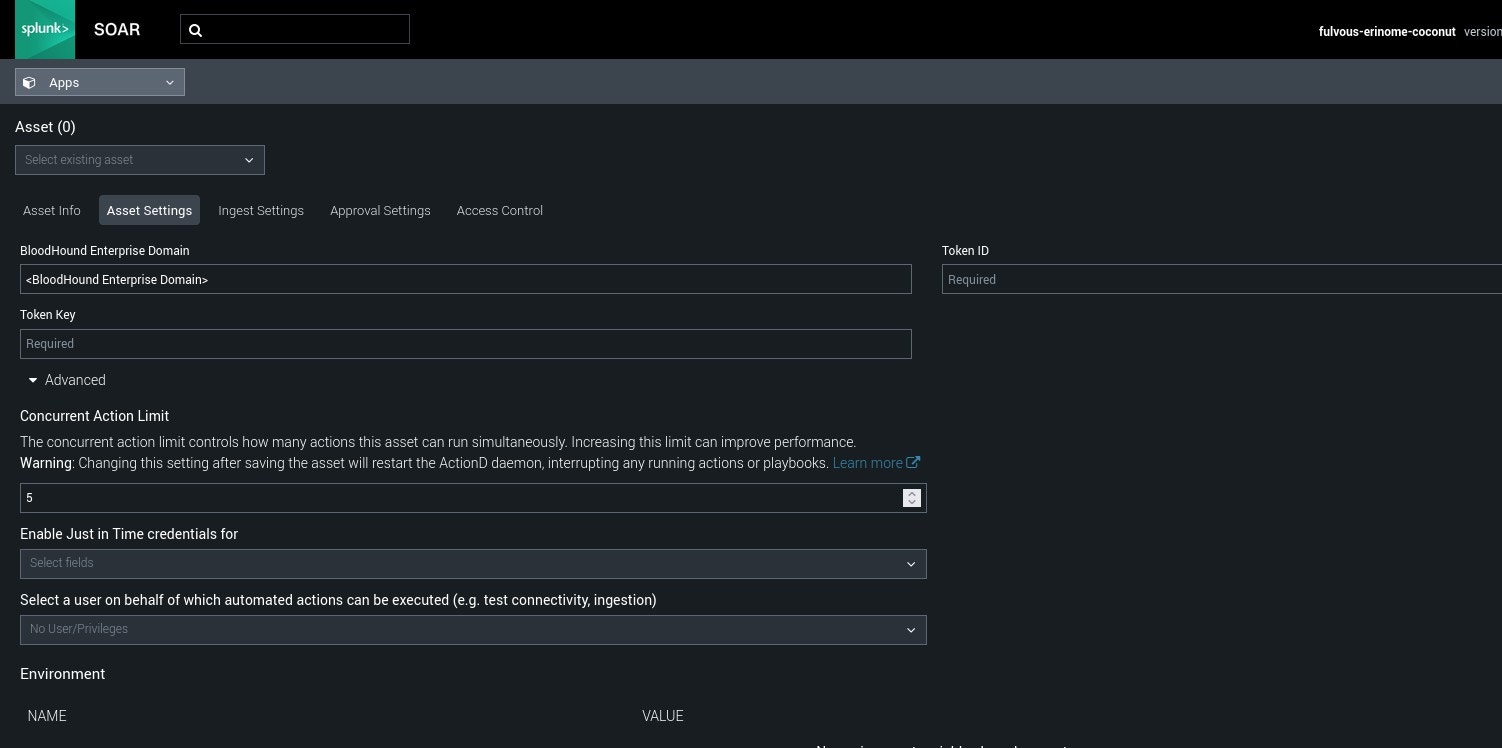
- Click Save.
Configure data ingestion
- Click Ingest Settings to set up how the app ingests data from BloodHound Enterprise.
-
Configure the following settings:
Field Description Label to apply to objects from this source Select events to label ingested data as events in Splunk SOAR Select a polling interval or schedule to configure polling on this asset Choose how often the app should poll BloodHound Enterprise for new findings. For testing, you can select Off and use manual polling. 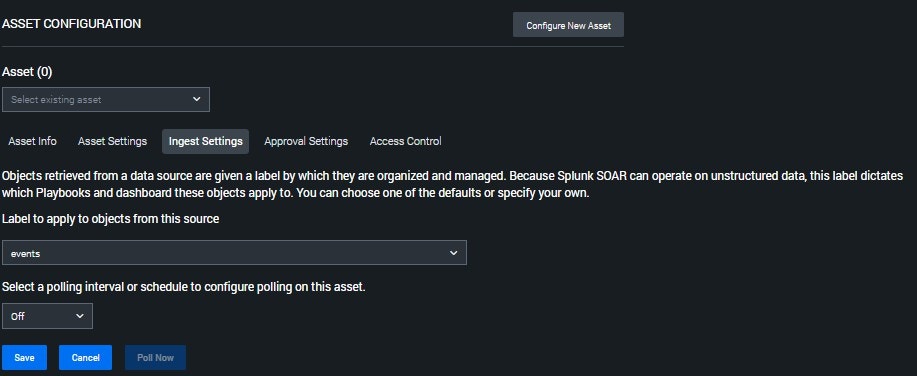
- Click Save.
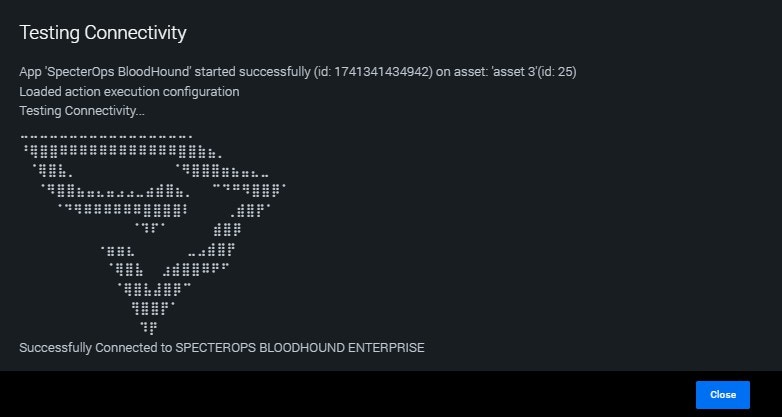
Test connectivity
Go back to Asset Settings and click Test Connectivity to verify the configuration.


Ingest data
If you set the polling interval to Off for testing, you can manually poll for events to start ingesting data from BloodHound Enterprise.
- Click Ingest Settings.
-
Enter the following values:
Field Description Maximum containers The maximum number of containers (event groupings) to ingest per polling cycle. Maximum artifacts The maximum number of artifacts (individual data items) to ingest per polling cycle. See the Splunk SOAR documentation for more information about these settings. -
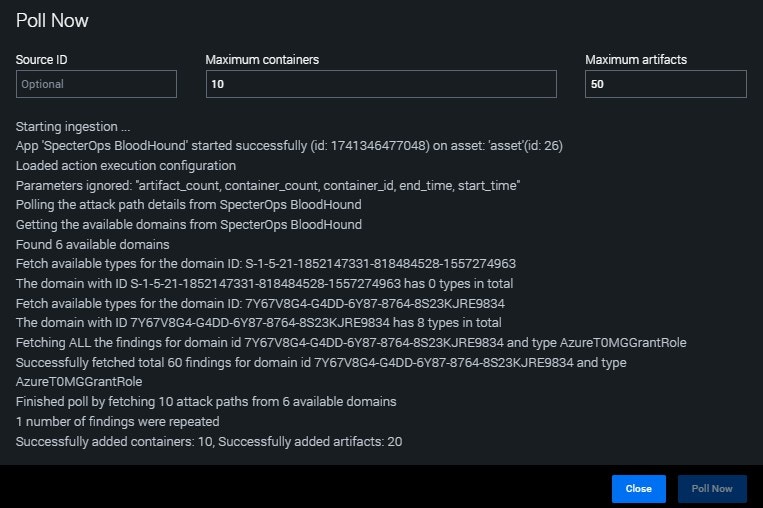
Click Poll Now.
After polling completes, confirm that containers and artifacts were added successfully, as shown below.

- Click Close.