- Create SIR ticketing workflows for BloodHound Enterprise attack path findings
- Integrate BloodHound Enterprise attack path findings into existing ticketing workflows
- Monitor identity vulnerabilities over time
Prerequisites
Before you begin the installation and configuration process, ensure the following prerequisites are met:- Admin access to a ServiceNow instance with the Security Incident Response (SIR) module installed and configured
- Access to the ServiceNow Store to install the BloodHound Enterprise app
- Admin access to a BloodHound Enterprise tenant
- A BloodHound Enterprise non-personal API key/ID pair with the Auditor role
Install the application
Installing the BloodHound Enterprise app on ServiceNow involves the following steps:Log in to ServiceNow
- Log in to your ServiceNow instance as an admin.
- Click System Applications > All Available Applications > All.
Search the ServiceNow Store
- In the search bar, enter SpecterOps BloodHound to find the app.
- Select the app from the search results.
Create an application user
The integration requires creating a user and assigning the role.Create a new user
The integration runs on behalf of the user account that you create in this step. It should be a dedicated service account associated with the non-personal API key/ID pair you created in BloodHound Enterprise.
- Click All > User Administration > Users.
- Click New.
- Enter required user details.
- Click Submit.
Configure the application
The integration provides a guided setup experience to connect to BloodHound Enterprise, filter attack path types, configure field mapping, and set the import schedule. Follow the steps below to complete the configuration.Change application scope
Before starting the configuration, change the application scope to to ensure that you have access to all necessary components and configurations.- Click the (globe) icon in the top-right corner and select Application Scope.
- In the search filter, enter and select it.
Connect to BloodHound Enterprise
The first step in the guided setup is to connect to your BloodHound Enterprise tenant by providing the tenant URL and API credentials.- In the top-left corner of ServiceNow, click All.
- In the search box, enter and select .
- Click Get Started in the Connect to SpecterOps BloodHound section to start the configuration process.
- Click Configure.
- Click New to add credentials.
- Enter your BloodHound Enterprise tenant URL, token key, and token ID and click Submit. The token key and ID refer to the non-personal API key/ID pair you created in BloodHound Enterprise. The tenant URL is the URL you use to access your BloodHound Enterprise tenant.
- Click the (close) icon.
- Click Mark as Complete to proceed to the next configuration step.
Filter attack path types
Next, configure filters to specify which attack path findings should create ServiceNow tickets. You can filter by environment and attack type to control the scope of findings that generate incidents.- Click Get Started in the Filter Attack Path Types section.
- Click Configure to select environments.
- Click New.
- Click the (lock) icon to select a single environment.
- After clicking the (lock) icon, click the (search) icon to display a list of available environments.
-
Click an environment to select it.
You must repeat steps 4-6 for each environment that you want to include.
- After selecting all required environments, click Submit.
- Click the (close) icon.
- Click Mark as Complete.
- Scroll down the page to the Filter Configuration section and click Configure.
- Click an environment to update the default configuration.
- Edit the fields as required.
- Click the Select All Attack Types checkbox to update finding types.
- Click Update to save the configuration.
- Click the (close) icon.
- Click Mark as Complete.
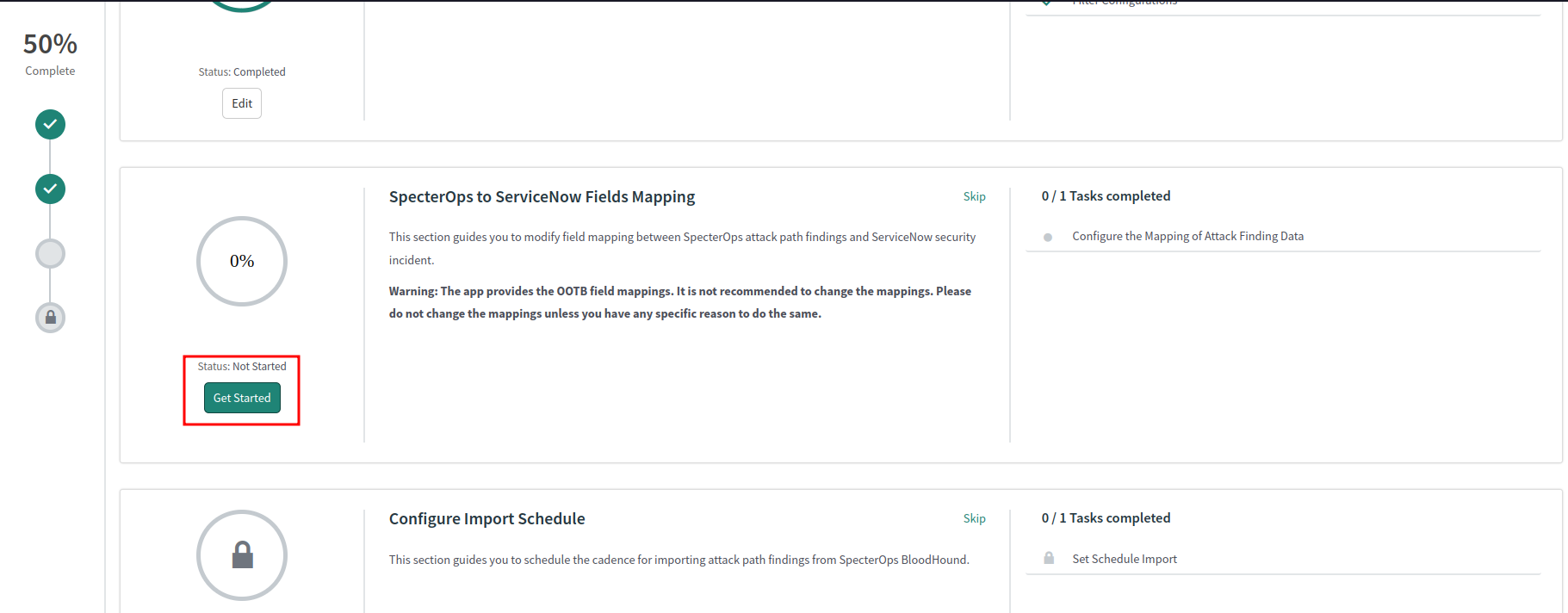
Configure field mapping
Field mapping allows you to specify how BloodHound Enterprise attack path finding fields map to ServiceNow SIR ticket fields. You can use the default mapping or customize it as needed.-
Click Get Started in the SpecterOps to ServiceNow Field Mapping section.
-
Click Configure to review the mapping. Update it if necessary, or use the default mapping.
The following table describes the default field mapping:
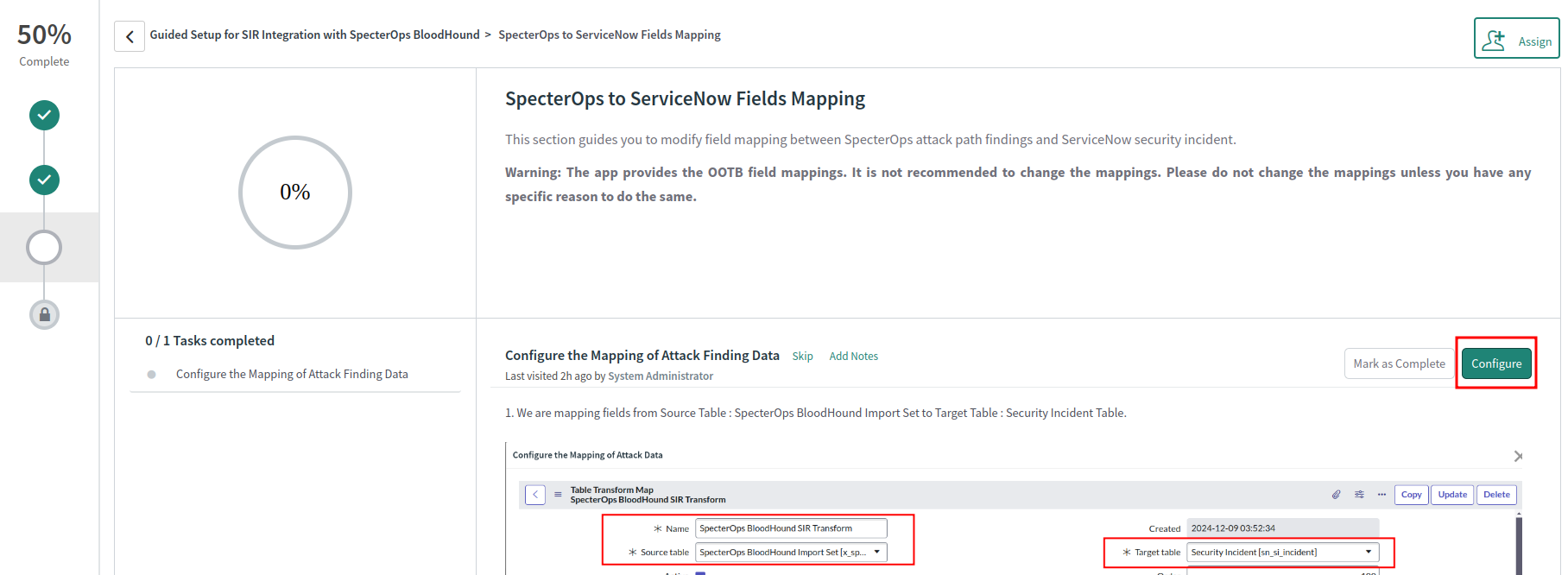
SpecterOps BloodHound Fields ServiceNow SIR Fields id correlation id composite risk risk score description + remediation description domain name + title + id short description from principal contact type server url external url - Click the (close) icon.
- Click Mark as Complete.
Configure import schedule
The final step in the guided setup is to configure the import schedule to specify how often the integration should fetch attack path findings from BloodHound Enterprise and create ServiceNow tickets.- Click Get Started in the Configure Import Schedule section.
- Click Configure to schedule an import.
- Click the Run dropdown menu and select one of the available options.
- Enter frequency details and click Update.
- Click the (close) icon.
- Click Mark as Complete.