Overview of gMSAs
Group Managed Service Accounts (gMSA) are managed domain accounts that provide automatic password management, simplified service principal name (SPN) management, and the ability to delegate the management to other objects. Detailed software requirements from Microsoft are available here. Microsoft gMSA documentation is available here.Create a gMSA account
To create a gMSA account, start by preparing the domain.- Log into a domain controller within the domain you want to create a gMSA.
-
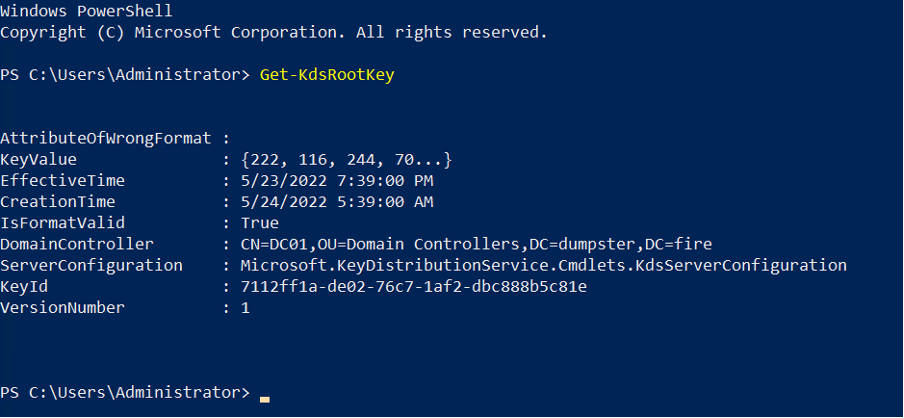
To validate whether the domain has a KDS Root Key configured, run:
If there’s no result returned, the KDS Root Key has not been configured in the domain. Continue on to step 3. If there is a result returned, the KDS Root Key has already been configured in the domain. Skip step 3 and move on to Create the gMSA and password read group.
-
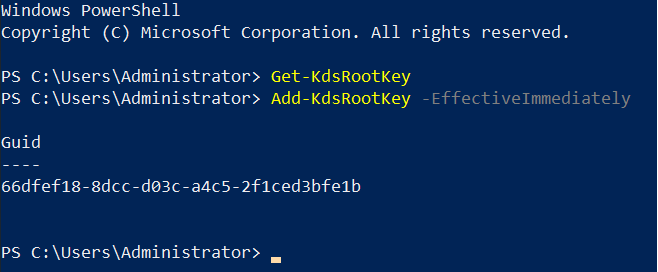
Create the KDS Root Key.
For a production environment, run:
For a test environment, make the key available for immediate use by running:
Create the gMSA and password read group
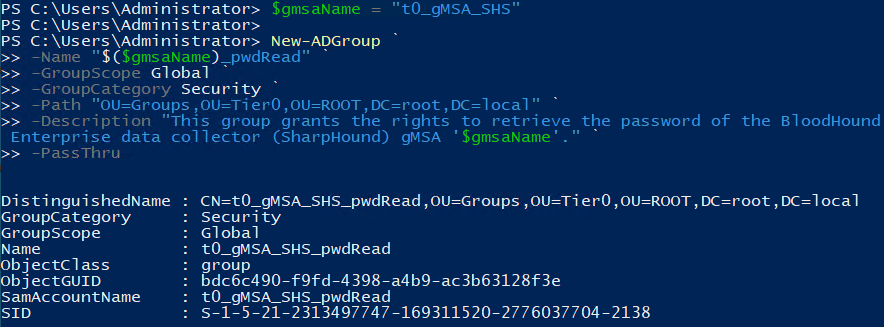
Perform these steps from/against a writeable Domain Controller.- Create a gMSA password read group for computers that should have access to the gMSA password. Browse to the desired location in Users and Computers and create the group. Alternatively, use this template to create the group using PowerShell:
-
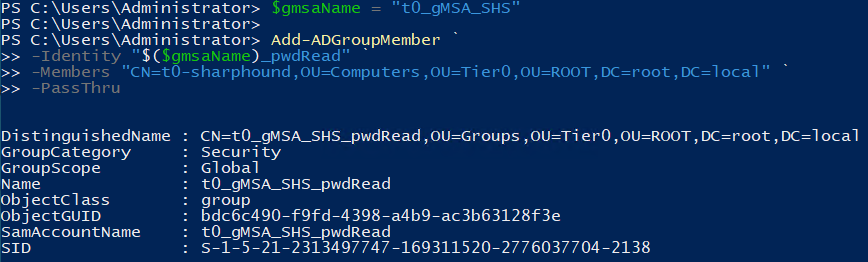
Add the SharpHound server that performs the Sharphound collections as a member of the gMSA password read group. This allows it to access the password of the gMSA and run the service.
Add the computer to the group in Users and Computers.
Alternatively, use this template to add group membership using PowerShell:
When viewing the changes on a Windows server with the GUI enabled, you can see the OUs and the t0_gMSA_SHS_pwdRead group you created.
-
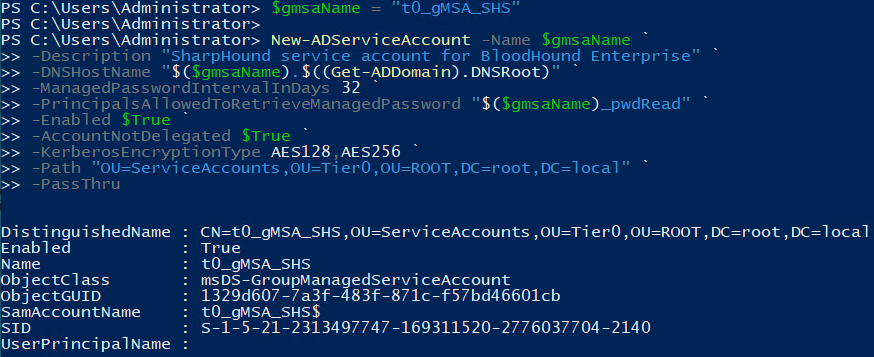
Create the gMSA and allow the password read group to retrieve its password.
On a Domain Controller, use this template to create the gMSA and set the retrieve right using PowerShell:
Prepare the SharpHound server
- Restart the SharpHound Enterprise server so that the server’s membership of the `pwdRead` group takes effect.
- Grant the gMSA the “Log on as a service” User Rights Assignment on the SharpHound server. This can be done through `secpol.msc` or policy deployment methods like a GPO.
- (Optional) Test that the SharpHound server can retrieve the gMSA password. See Test the gMSA.
Test the gMSA
Optionally test the gMSA server to make sure that the gMSA is working.-
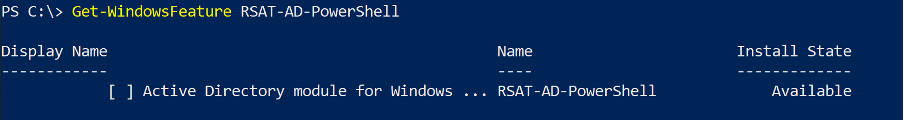
Check the status of the RSAT PowerShell module. On the SharpHound Enterprise server, open a PowerShell as an Administrator and run:
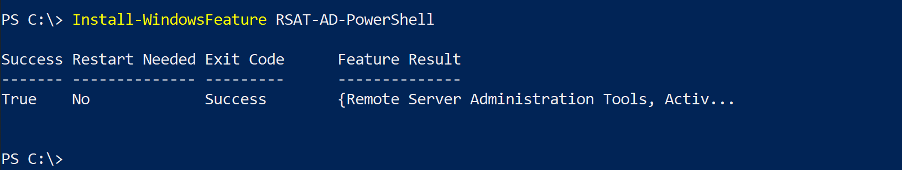
If the Install State shows “Installed”, skip to step 2, otherwise run:
-
In the elevated PowerShell, test that the SharpHound server can retrieve the gMSA password by running:
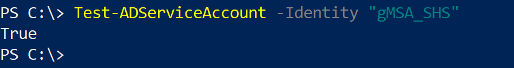
True.
The gMSA is now ready to be used on the SharpHound Enterprise server. Follow Install and Upgrade SharpHound Enterprise to complete the installation of the SharpHound Enterprise service.
Add the gMSA to the SharpHound Enterprise service
Change the SharpHound Enterprise service to be run by the created gMSA. This can be done in two ways:Using Services GUI / ‘services.msc’
- Open the Services application / ‘services.msc’ as a local administrator.
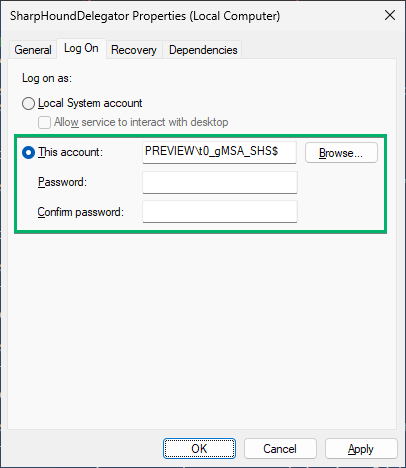
- Open properties of the service: SharpHoundDelegator.
- In the Log On tab, set This account to be the gMSA.
- Delete the contents of the password fields if present.
- Save by clicking OK.
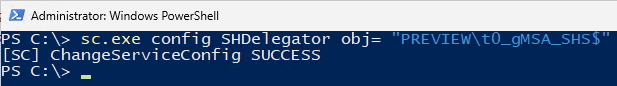
Using command line / ‘sc.exe’
- Open the command prompt/PowerShell as a local administrator.
- Run the following command, replacing the ‘DOMAIN’ and gMSA name to match your environment.