Create the AzureHound Enterprise app
- Log into the Microsoft Entra admin center as a user with the Global Administrator role, or the following less privileged roles:
-
In the left menu, select App registrations.
-
Click New registration.
-
In the Name field, give the application an identifying name in your organization. Make sure the supported account type is set to the “Accounts in this organizational directory only (Single tenant)” option. A URI is not required. Then click Register.
-
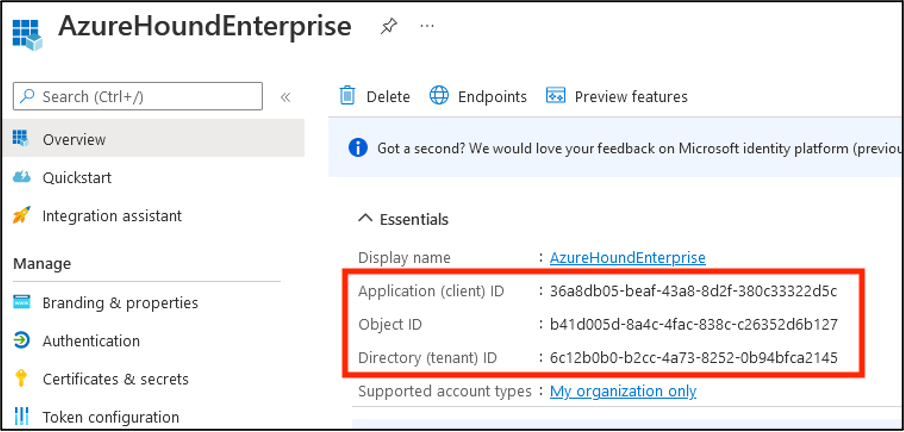
In the Overview menu, copy the Application (client) ID and Directory (tenant) ID to be used later in AzureHound Enterprise Local Configuration.
- Continue to the next section: “Grant Microsoft Graph Permissions”.
Grant Microsoft Graph Permissions
-
In the AzureHound application, select API Permissions.
-
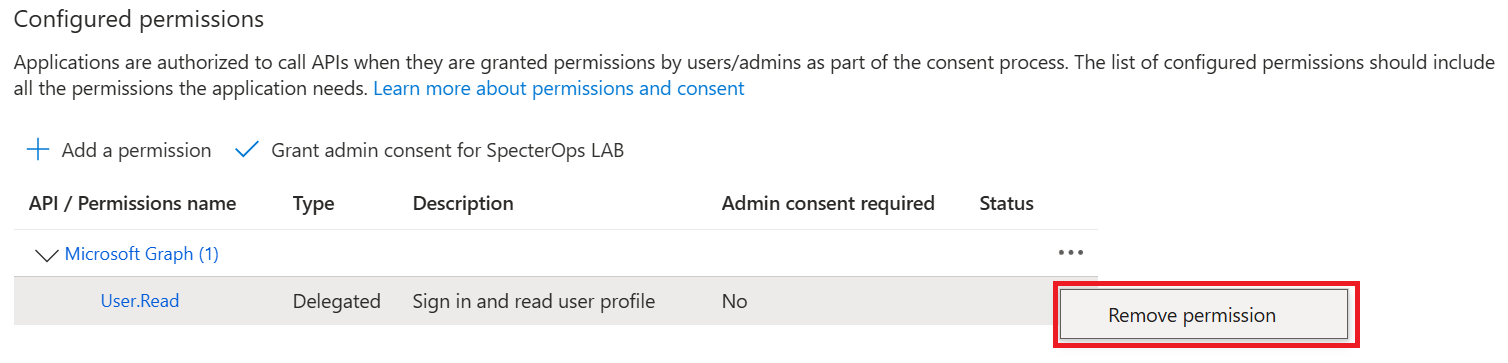
Remove the default User.Read delegated permission from the application, as it is not needed for data collection. Confirm the operation in the dialog window that appears after selecting the Remove permission option from the context menu.
-
Select Add a permission.
-
Click on Microsoft Graph.
-
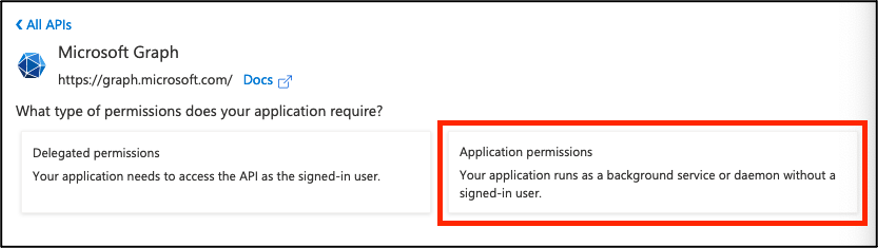
Select Application permissions.
-
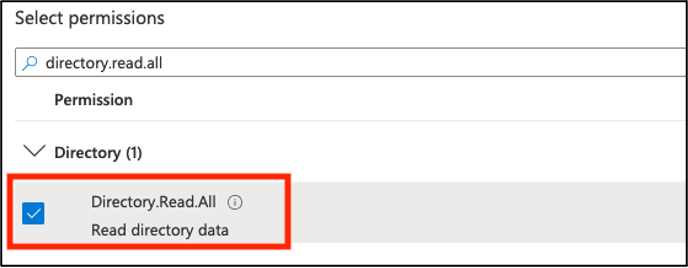
Search for the Directory.Read.All permission and check the box next to it.
-
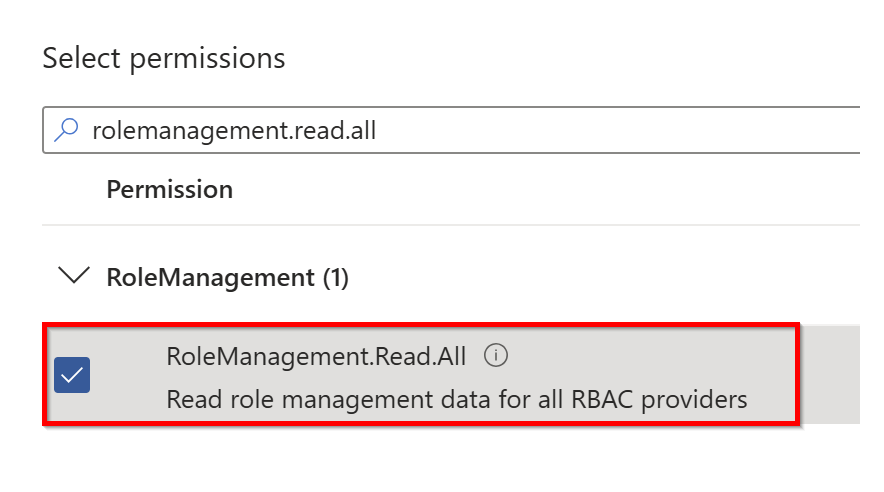
Search for the RoleManagement.Read.All permission and check the box next to it.
-
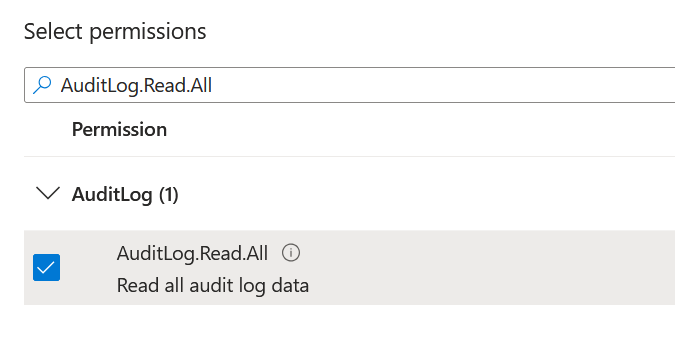
(Optional step to collect AZUser.LastSuccessfulSignInDateTime) Search for the AuditLog.Read.All permission and check the box next to it.
-
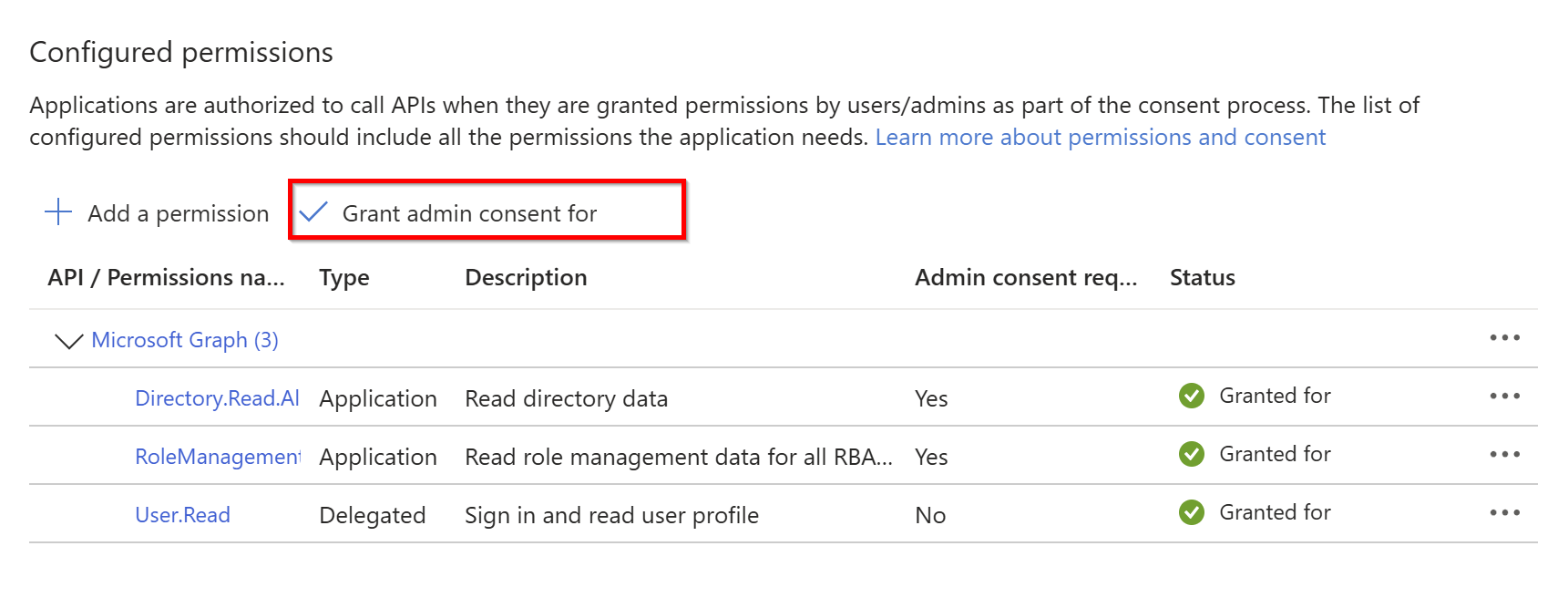
In the bottom of the window, select Add permissions.

- Click on Grant admin consent for <your_tenant_name>.
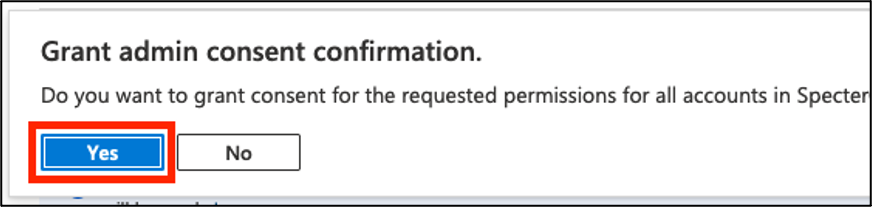
- Click Yes on the confirmation dialog.
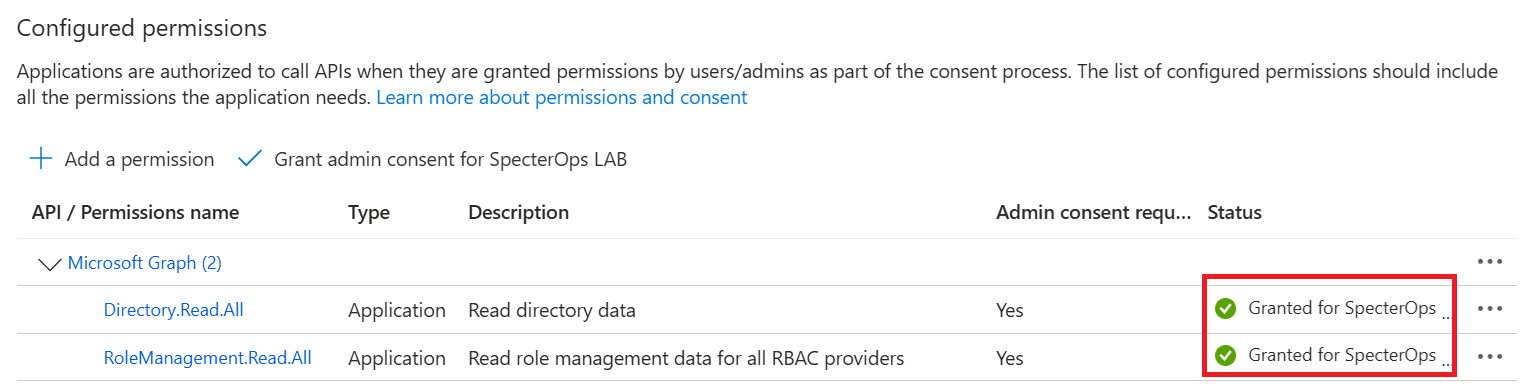
- After being redirected to API Permissions again, you should see both permissions as Granted.
- Continue to the next section: “Add application authentication certificate”.
Add application authentication certificate
This section requires you have authentication material. We highly recommend using certificate-based authentication. If you do not already have a certificate created, follow the article AzureHound Enterprise Local Configuration and then return back here.-
Select the Certificates & secrets section on the left.
-
Click on Certificates.
-
Click Upload certificate.
- Locate the cert.pem file created during AzureHound setup (either on your own, or utilizing the instructions at AzureHound Enterprise Local Configuration).
-
Click the folder icon and locate the “cert.pem” file. Add a description if desired.
- In the bottom of the window, select Add.
- Continue to the next section to optionally configure application branding.
Configure application branding (optional)
Note: All steps in this section are optional and do not affect the functionality of the collector.- Download the AzureHound Enterprise icon to your computer.
-
Still on the AzureHound application in the Entra ID admin center, open the Branding & properties section.
-
Click the Select a file button and browse to the file you previously downloaded.
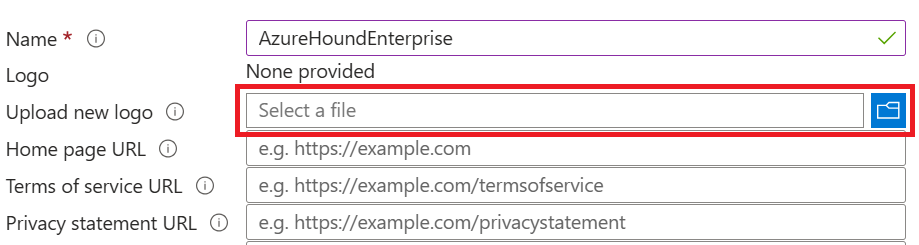
- Provide a human-readable Name for the application, e.g., BloodHound Enterprise Collector (AzureHound).
- Type your BloodHound Enterprise tenant URL into the Home page URL field. This is for record keeping only.
-
Click the Save button and review the results.

- Continue to the next section to assign the Directory Readers role on your Entra ID tenant.
Assign “Directory Readers” role on the Entra ID tenant
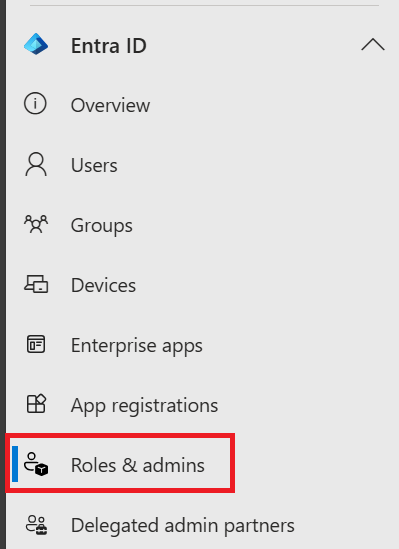
- In the left menu, select Roles & admins.
-
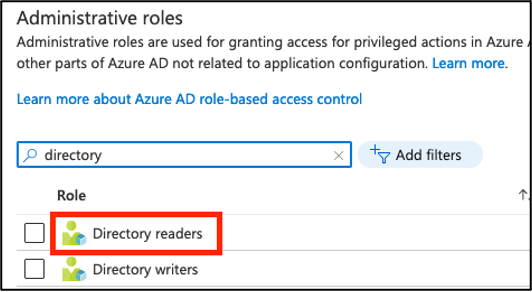
Search for the role Directory Readers and click the role name or description.
Note: Clicking the checkbox sometimes prevents clicking on the role itself.
-
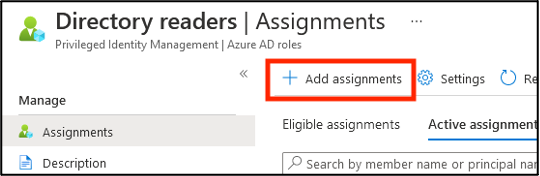
In the “Directory Readers” role, select Add assignments.
-
Click No member selected to open the search window.
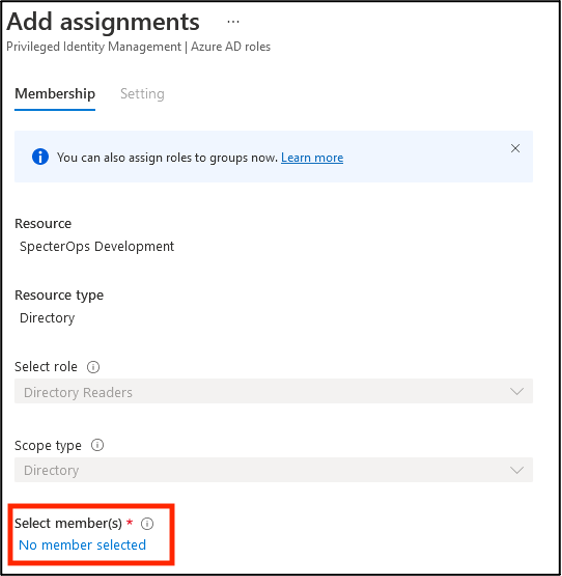
-
Search for the previously created service principal with either its name, application ID, or object ID. Select it by clicking on it.
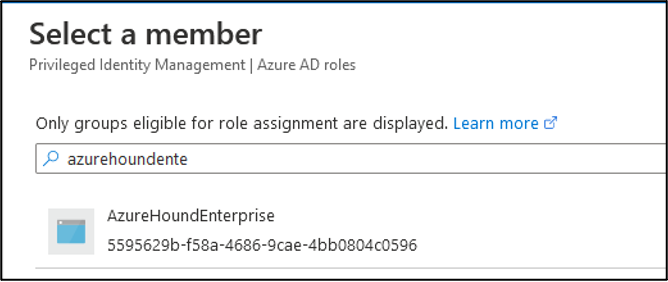
-
Click Select.
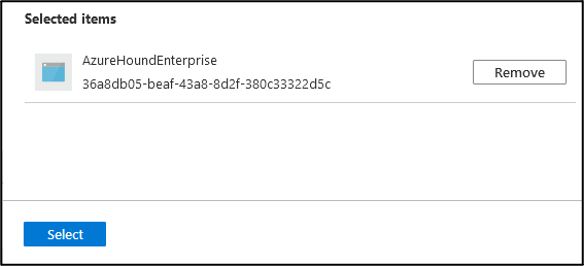
-
Validate that your principal is displayed and click Next.
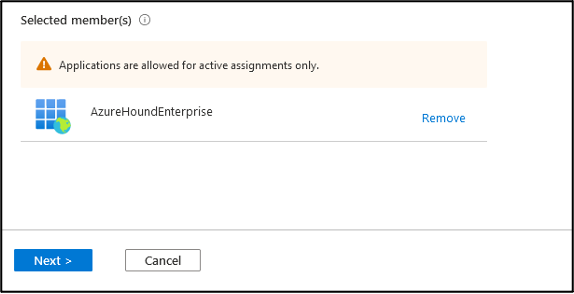
-
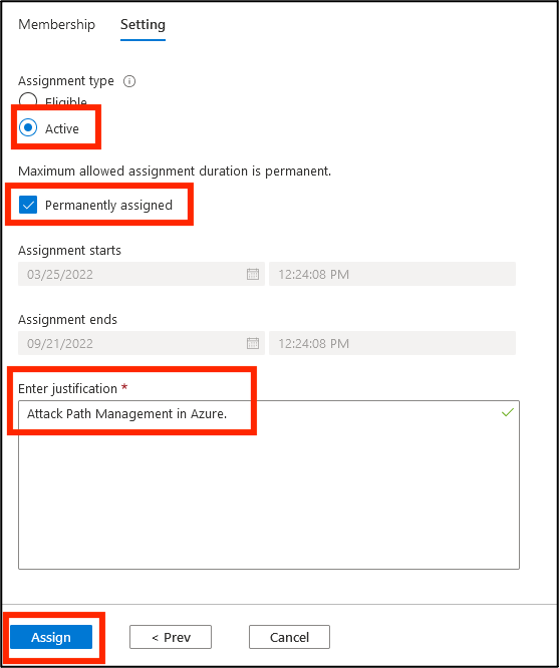
Ensure that the Assignment type is Active and the Permanently assigned box is checked. Provide a justification and click Assign.
- Confirm the service principal is a Directory Reader by refreshing this view.
- Continue to the next section to assign the Reader role on your Azure subscriptions.
Grant “Reader” role on all Azure subscriptions
Note: If you do not have any management groups, you may either create your Tenant Root Group following the prompts in the middle of the screen to ensure future visibility if another administrator begins use of subscriptions, or you may skip this section altogether. If you skip this section, you will see a warning in the logs for each collection indicating the lack of ability to collect this data accordingly.- Log into the Azure portal as a user with the User Access Administrator role.
-
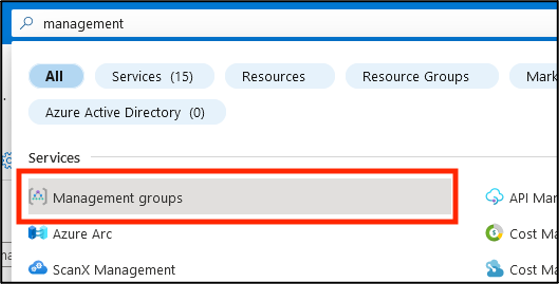
Search for and select the Management groups item in the top search bar.
-
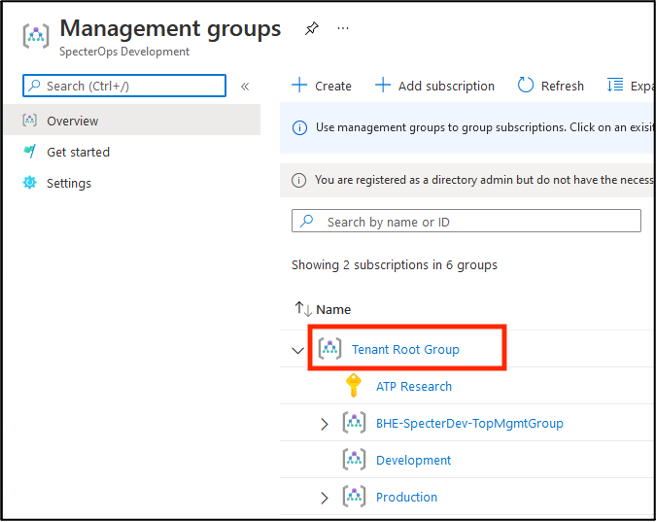
Select Tenant Root Group.
-
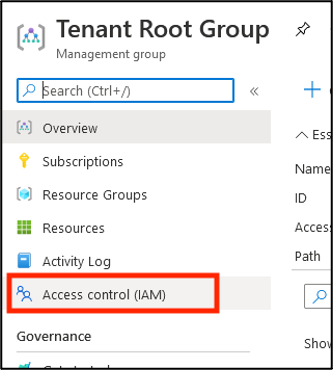
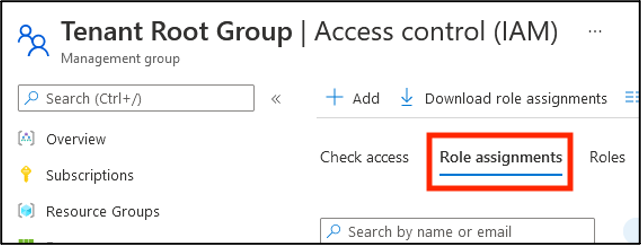
Select Access control (IAM).
-
Select Role assignments.
-
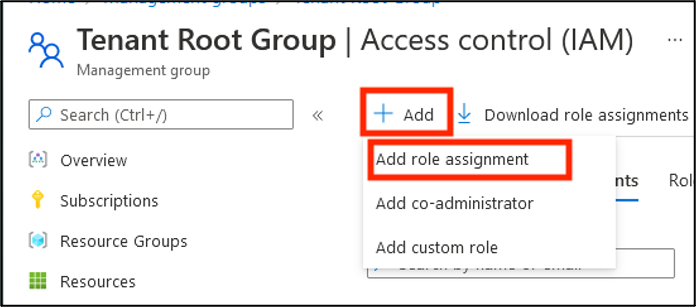
Click Add, then Add role assignment.
-
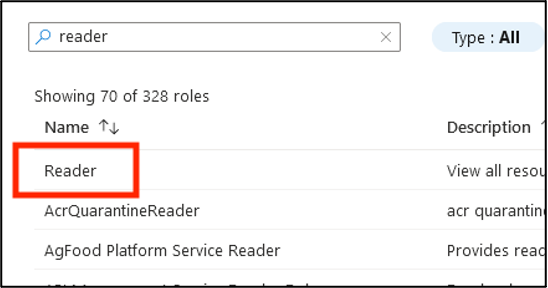
Find the Reader role and select it.
-
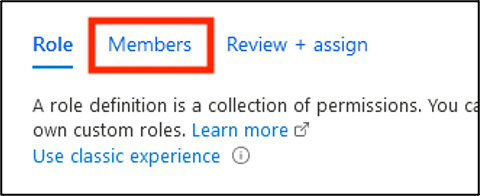
Click Members.
-
Click Select members.
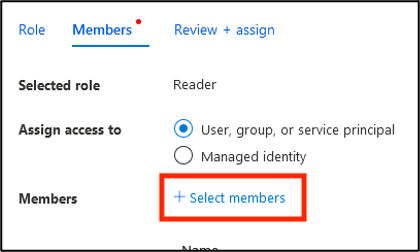
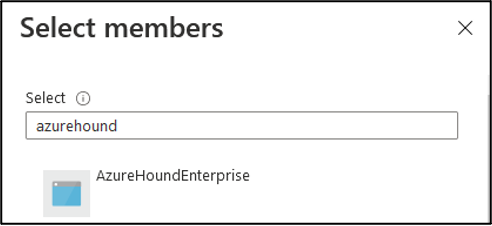
- Search for and click on your previously created service principal.
-
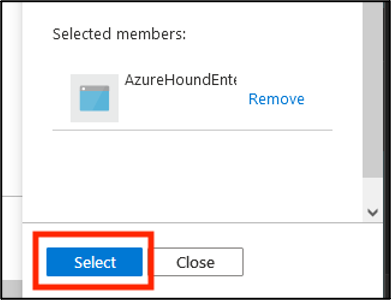
Validate the principal selected, then click Select.
-
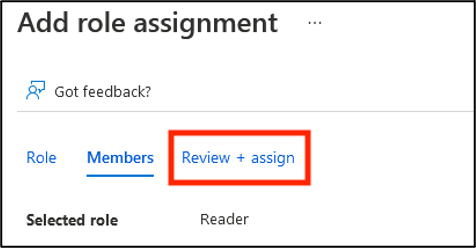
Click the tab Review + Assign.
-
Click Review + Assign at the bottom of the page.
- Confirm the role is present by refreshing this view. You may need to alter the filter to see this role.
- Continue to Run and Upgrade AzureHound (Windows, Docker, or Kubernetes)